As part of our consultation, we have done security assessments in industries such as Finance, Health Care, Retail and Technology.
Services:
• Web Application Penetration Test
• API Penetration Test
• IOS & Android Penetration Test
• Network Penetration Test
• Red Team Assessments
• Social Engineering Scenarios (Phishing/Spear Phishing/ Vishing)
The Methodology we follow:
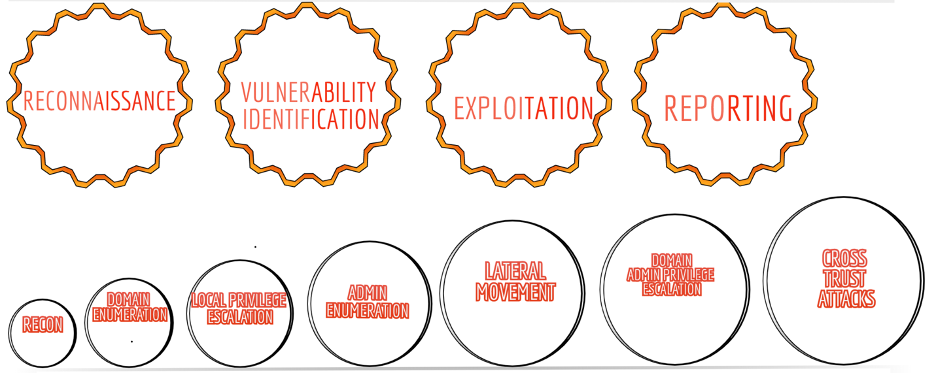
• Reconnaissance - This process begins with getting to know the target using passive methods and network scanning.
• Vulnerability Identification – This process identifies valid findings from the scans to further exploit manually for the purpose of detecting security weaknesses in the application.
• Exploitation – At this stage the security consultant safely exploits the identified vulnerability to gain access by breaching security of a system. Once, the access is acquired, the focus turns to escalation and movement to identify technical risk and total business impact.
• Reporting - Detailing the vulnerabilities found and providing information on potential impact on the company if exploited.
For any Security Consultation, send me an email via @[email protected]
