AI-ThreatMaster - An AI Powered Threat Modelling Tool

Introduction
I stumped upon STRIDEGPT and wanted to create a tool that align Threat Modelling with the OWASP Top 10 methodology. The tool generate threats and mitigation based on a description provided by a user. A framework such as OWASP top 10 can be used by organizations to maintain consistency and alignment when mapping vulnerabilities from different sources like penetration testing, dynamic application security testing (DAST) scans and Threat Modelling.
Proof of Concept: AI-ThreatMaster
Source Code: AI-ThreatMaster
OWASP AI-ThreatMaster: AI-ThreatMaster
Benefits of Standardized Threat Modeling
OWASP Top 10 is widely adopted across the security landscape. By aligning threat models with these standards, AI-ThreatMaster offers several advantages:
- Standardization: Standardizing threat models enhances consistency and understanding across teams.
- Efficiency: Allows easy mapping of identified vulnerabilities to well-defined categories.
- Integration: Facilitates integration with existing vulnerability management practices.
Embracing AI for Threat Modeling
AI-ThreatMaster leverages AI-powered threat modeling, utilizing OpenAI’s GPT models. This not only standardizes the process but also minimizes the human bias involved in threat identification. Many organizations have opted to disable ChatGPT to prevent potential misuse, the way AI-ThreatMaster is designed, it limit the exposure solely to threat modeling, it enables engineers to adopt the tool while mitigating the misuse of AI capabilities.
Additionally, using an AI-powered threat modeler offers several advantages over manual threat generation. First, it significantly reduces time and effort, enabling quicker identification of potential threats and their mitigations. Additionally, AI models continuously learn from vast datasets, staying updated with emerging threats.
Manual threat generation involves extensive human resources, including skilled security analysts. It demands ongoing training and expertise, incurring high labor costs. Conversely, while initial investment might be necessary for AI implementation, long-term costs are comparatively lower, mainly through reduced human labor and scalability
OWASP TOP 10 in SDLC PIPELINE
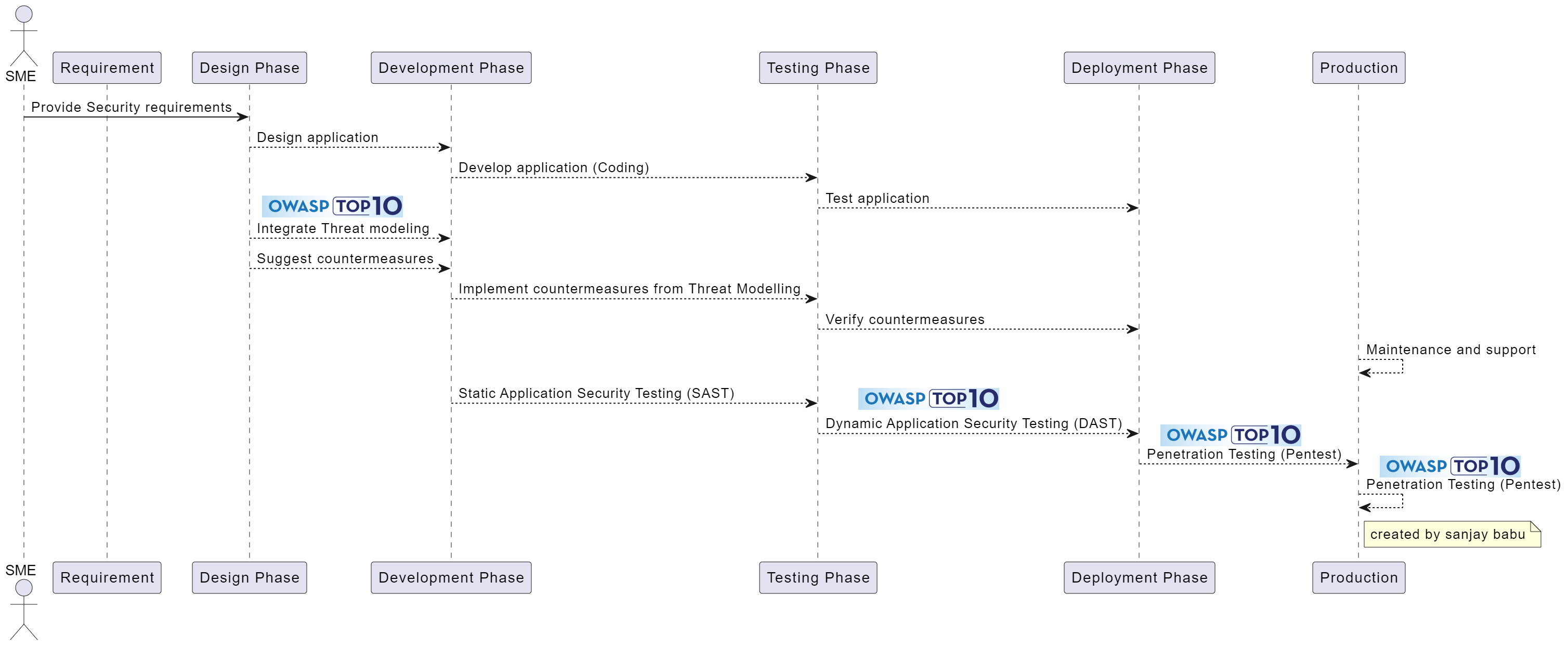
Leveraging OWASP Top 10 Methodology
Web Application Risks (OWASP Web Top 10)
- Broken Access Control: A01:2021
- Cryptographic Failures: A02:2021
- Injection: A03:2021
- Insecure Design: A04:2021
- Security Misconfiguration: A05:2021
- Vulnerable and Outdated Components: A06:2021
- Identification and Authentication Failures: A07:2021
- Software and Data Integrity Failures: A08:2021
- Security Logging and Monitoring Failures: A09:2021
- Server-Side Request Forgery: A10:2021
Mobile Application Risks (OWASP Mobile Top 10)
- Improper Credential Usage: M1
- Inadequate Supply Chain Security: M2
- Insecure Authentication/Authorization: M3
- Insufficient Input/Output Validation: M4
- Insecure Communication: M5
- Inadequate Privacy Controls: M6
- Insufficient Binary Protections: M7
- Security Misconfiguration: M8
- Insecure Data Storage: M9
- Insufficient Cryptography: M10
Desktop Application Risks (OWASP Desktop Top 10)
- Injections: DA1
- Broken Authentication & Session Management: DA2
- Sensitive Data Exposure: DA3
- Improper Cryptography Usage: DA4
- Improper Authorization: DA5
- Security Misconfiguration: DA6
- Insecure Communication: DA7
- Poor Code Quality: DA8
- Using Components with Known Vulnerabilities: DA9
- Insufficient Logging & Monitoring: DA10
Cloud Application Risks (OWASP Cloud Top 10)
- Insecure cloud, container, or orchestration configuration: CNAS-1
- Injection flaws (app layer, cloud events, cloud services): CNAS-2
- Improper authentication & authorization: CNAS-3
- CI/CD pipeline & software supply chain flaws: CNAS-4
- Insecure secrets storage: CNAS-5
- Over-permissive or insecure network policies: CNAS-6
- Using components with known vulnerabilities: CNAS-7
- Improper assets management: CNAS-8
- Inadequate compute resource quota limits: CNAS-9
- Ineffective logging & monitoring (e.g., runtime activity): CNAS-10
API Risks (OWASP API Top 10)
- Broken Object Level Authorization: API1:2023
- Broken Authentication: API2:2023
- Broken Object Property Level Authorization: API3:2023
- Unrestricted Resource Consumption: API4:2023
- Broken Function Level Authorization: API5:2023
- Unrestricted Access to Sensitive Business Flows: API6:2023
- Server Side Request Forgery: API7:2023
- Security Misconfiguration: API8:2023
- Improper Inventory Management: API9:2023
- Unsafe Consumption of APIs: API10:2023
IoT Risks (OWASP IoT Top 10)
- Weak, Guessable, or Hardcoded Passwords: I1
- Insecure Network Services: I2
- Insecure Ecosystem Interfaces: I3
- Lack of Secure Update Mechanism: I4
- Use of Insecure or Outdated Components: I5
- Insufficient Privacy Protection: I6
- Insecure Data Transfer and Storage: I7
- Lack of Device Management: I8
- Insecure Default Settings: I9
- Lack of Physical Hardening: I10
